This guide describes common MFA use-cases and their solutions within the Cloudentity stack.
|
Note
|
Each flow may be handled using the appropriate Cloudentity UI, or through direct API calls. These distinctions are made clear throughout this guide. |
General
MFA flows begin with an initial, single-factor authentication. Identifier + password authentication is commonly used as the first factor, although other options exist such as federated login using SAML. The session token generated by a successful authentication may then be used for upgraded authentication using any of the MFA techniques. The flows described here assume that a valid session token has already been created for the user by some means.
|
Warning
|
The term "multi-factor" implies that some "first factor" of authentication has been satisfied. However, some of the advanced authentication techniques described in this document may be used as the first factor (in lieu of password or other common authentication techniques) for certain use-cases. For example, the API "Identifier + TOTP Authentication" exists for such cases. In general, in this document the term "MFA" will be used in the context of stepped-up, non-first-factor authentication. |
Time-based One-Time Password (TOTP)
Time-based One-Time Password (TOTP) Authentication uses the current time to generate a random code based on some secret only made known to the user. If the user submits the code and it matches the system-generated code corresponding to that user account, the user’s identity is trusted and authentication succeeds. The code is only valid for a short period of time (typically 30 seconds) before a new code is generated.
Any application which supports TOTP may be used for TOTP Authentication in the Cloudentity system. Mobile apps which support TOTP include:
-
Google Authenticator (GA): available for free at Google Play or the App Store. Google Authenticator is used throughout this document.
-
Microsoft Authenticator: available for free at Google Play or the App Store.
By entering the TOTP secret into the mobile app, the app can consistently supply up-to-date codes which the user may submit for authentication.
|
Warning
|
The original name of TOTP Authentication in the Cloudentity stack was "Google Authentication". This name can still be found in various places in the stack, for backward-compatibility reasons; for example, the value of mfaMethod corresponding to TOTP MFA is "GOOGLE_AUTHENTICATION".
|
|
Note
|
Relevant user attributes for TOTP MFA:
|
TOTP Setup
A setup phase is required before TOTP can be used for authentication.
1. Initializing the TOTP secret
When a new user is registered in the Cloudentity system, a TOTP secret (attribute name googleAuthSecret) is generated and stored with the user record. The user’s googleAuthSecretAccepted status is also initialized to "false".
2. Retrieving the TOTP secret
The TOTP secret can be viewed by an authenticated user through the self-service "Get Auth Secret" API:
In the AuthN UI, TOTP users whose TOTP secret has not yet been accepted will be guided to the "TOTP Authentication Setup" screen to retrieve the TOTP secret:
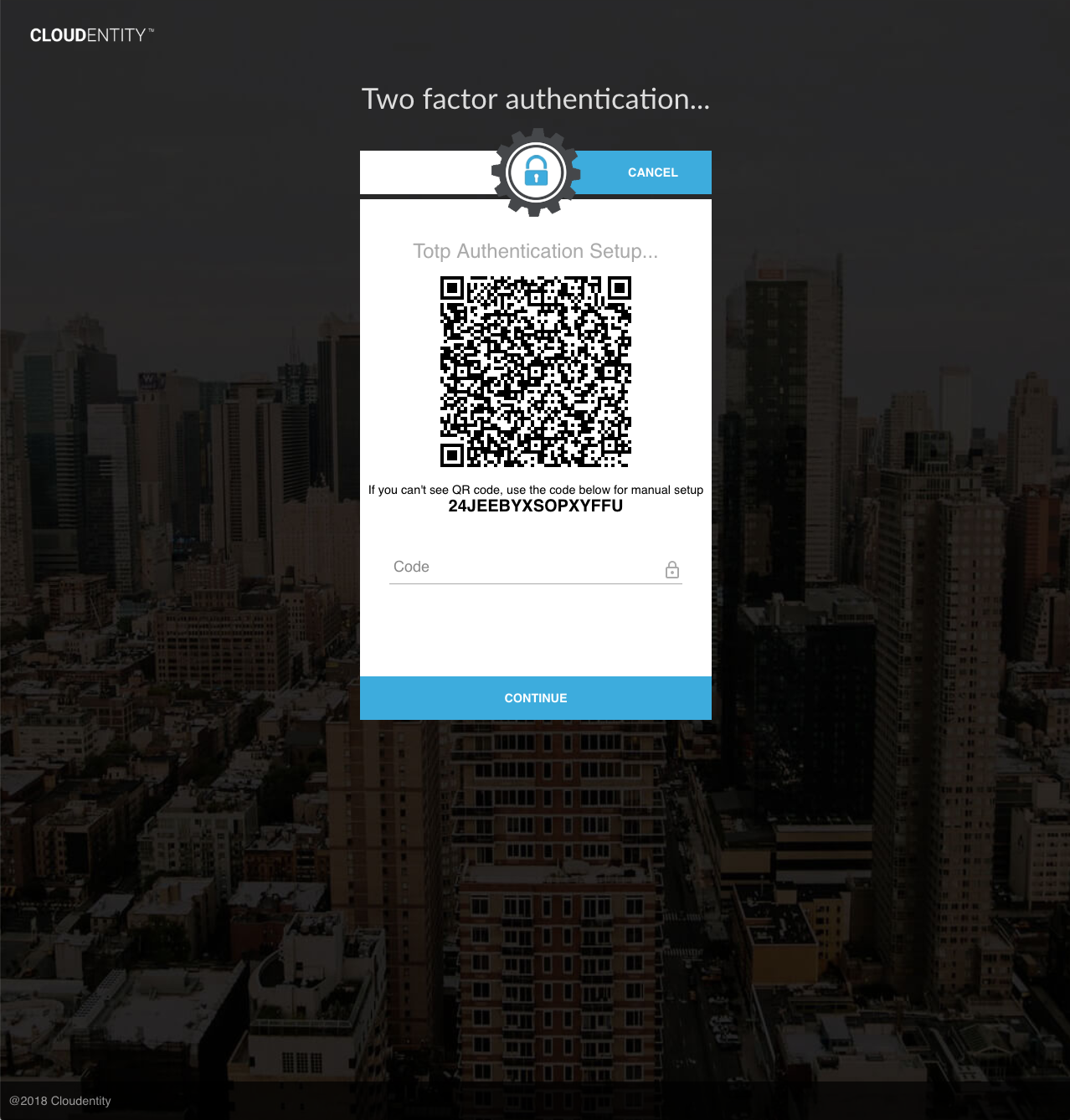
|
Note
|
The TOTP secret (
|
3. Setting up TOTP Generation
The user must enter the TOTP secret into the TOTP mobile app or system to continue:
The user may select either of two setup types: "Scan barcode" or "Manual entry":
If the user’s mobile device has a QR code scanner, the QR code from the UI may be scanned to automatically record the username and TOTP secret:
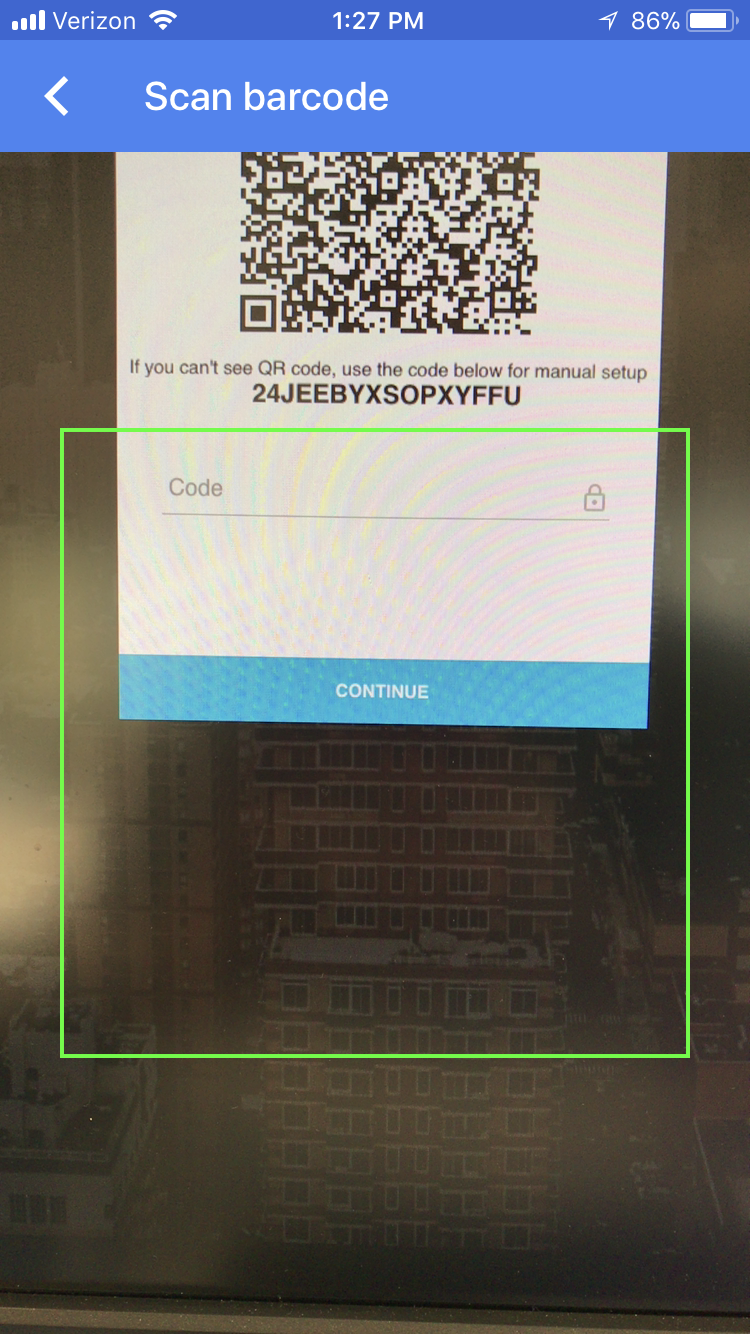
If the user chooses not to use the QR code scanner, the TOTP secret may be entered manually:
Once the TOTP secret is entered, the TOTP app will begin to generate TOTPs:
4. TOTP confirmation
Before the TOTP can be used for authentication, the user must confirm that it has been set up properly by successfully submitting a TOTP code. This is done through the self-service "Confirm Auth Secret" API:
The TOTP may also be entered through the Authn UI’s TOTP Setup page.
Upon success, the user’s googleAuthSecretAccepted is set to "true", preventing further retrieval of the googleAuthSecret. An auth event may also be generated for this session indicating that the TOTP secret was confirmed.
|
Tip
|
Configuration Tip: Confirm Auth Secret
The relationship between TOTP secret confirmation and the overall authentication flow may be controlled by several options:
|
TOTP Authentication
Once TOTP setup is completed, the user may authenticate using TOTP.
Using the AuthN UI, the user must enter a valid TOTP generated from the TOTP app to proceed:
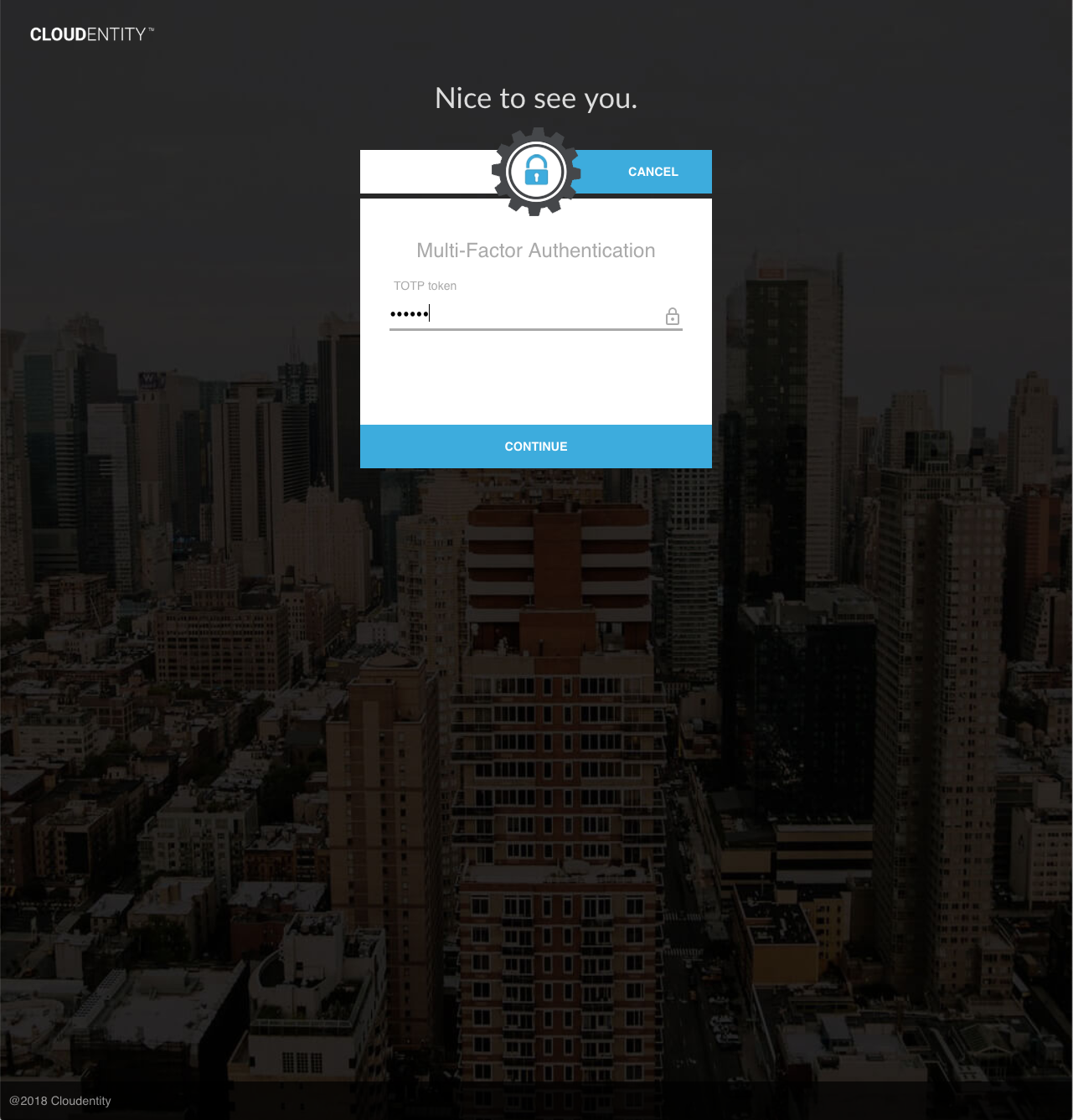
Upon success, a TOTP Authentication auth event is generated for the current session. Authorization policies which require this event will pass for this session.
TOTP Management
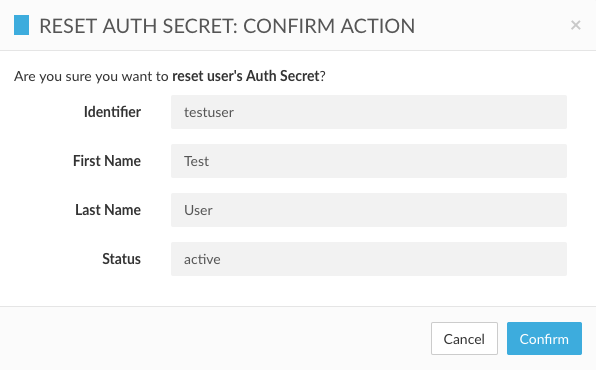
In order to protect a user account whose TOTP secret may have been compromised, it is possible to regenerate a TOTP secret for a user. An administrative user may reset the TOTP secret for a user using the administrative "Reset Auth Secret" API.
In the Administrative UI, the admin can perform this action in the User menu:
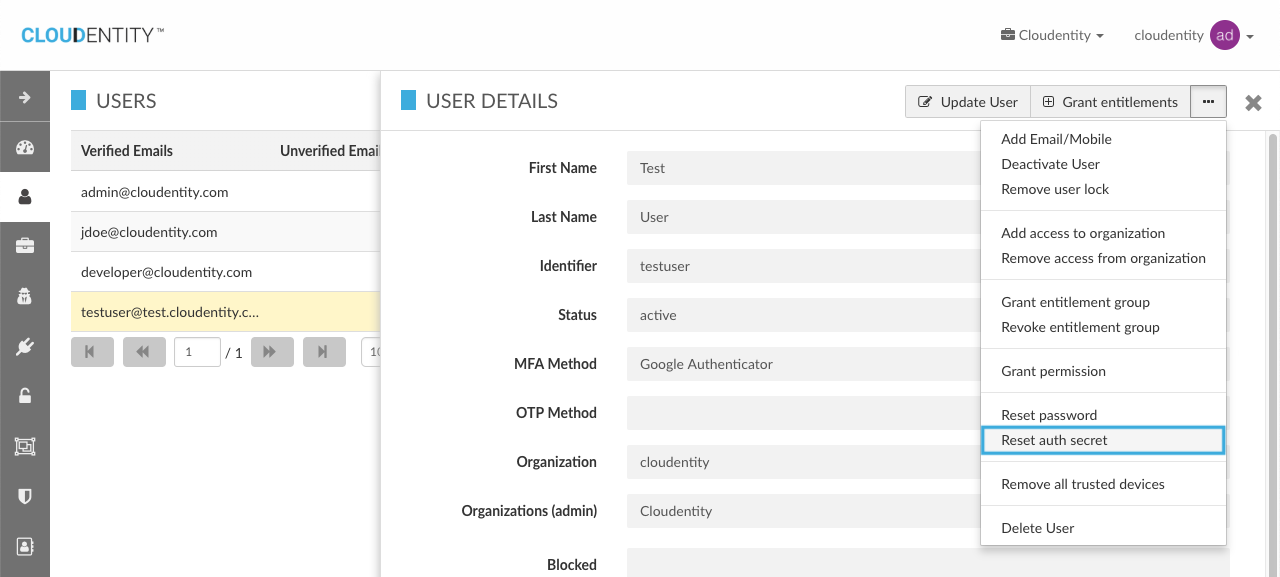
The action is completed once the admin clicks "Confirm":
Alternatively, an authenticated user may reset the TOTP secret using the self-service "Self Reset Auth Secret" API.
Upon success, a new TOTP secret is generated and stored in the user’s googleAuthSecret attribute, and TOTP confirmation is cleared (googleAuthSecretAccepted is reset to "false"). The user must complete TOTP setup again to be able to perform TOTP authentication.
One-Time Password (OTP)
One-Time Password (OTP) Authentication is achieved when a one-time password (OTP), generated and sent to the user via some messaging method, is correctly returned by the user as an authentication credential. Because the user is the owner of the destination address to which the OTP is sent, when the OTP is submitted correctly the user’s identity is trusted.
In the Cloudentity stack, the following messaging methods are available:
-
Email
-
SMS
-
Voice message
|
Note
|
Relevant user attributes for OTP MFA:
|
The flows described below are organized into several categories:
-
Explicit destination: The destination address is specified in the request.
-
Implicit destination: The destination address is inferred from the user’s
otpMfaDestinationandotpMethodattributes (not available during first-time OTP setup). -
Masked destination: A masked identifier key is generated for the destination address and is submitted instead of the destination address itself.
OTP Setup
A setup phase is required before OTP can be used for authentication.
1. Generating and sending the setup OTP
The first step in OTP MFA authentication is to verify that the user is able to receive OTPs at the desired destination. The OTP can either be sent according to the explicit destination flow, or the masked destination flow.
|
Note
|
Certain UI flows may skip this step, if the user already has a verified identifier email or mobile. |
1a. Explicit destination flow
For the explicit destination flow, an OTP must be generated and delivered to the destination using the self-service "Setup OTP MFA" API.
Upon success, an OTP is generated and sent to the requested destination, using the requested messaging method. The destination and delivery method are stored in the user’s otpMfaDestination and otpMethod attributes, respectively, and the user’s otpSetupComplete is set to false. If the destination address was not already a registered address for the user, it will be automatically added as an unverified email or mobile of the user (based on the requested destinationType).
If an OTP has already been sent to the user, the request may be replayed by calling the "Setup OTP MFA" API with an empty request body — in this case, the user’s otpMfaDestination and otpMethod will be used to generate and send an OTP to the original destination by the original method.
|
Tip
|
Configuration Tip: Send OTP Parameters
In the Cloudentity User Service, many APIs are capable of sending messages to users by various means ("message-sending" APIs). The OTP action ID and expiration time may be independently configured for each of these APIs. For example, an API which generates OTPs used for MFA, expiring in 15 minutes, would have the following configuration: otp {
<api_identifier_key> {
action = "mfaChallenge"
expirationTimeInMinutes = 15
}
...
}
|
|
Tip
|
Configuration Tip: Send Info
For each message-sending API, a system configuration exists to enable or disable the inclusion of details about the delivery in the response body. sendInfo {
<api_identifier_key> {
returnSendInfo = true|false
maskDestinationInResponse = true|false
}
...
}
If Example response body when {
"destination": "*******3567",
"destinationType": "MOBILE",
"deliveryMode": "SMS",
"codeType": "PLAINTEXT"
}
|
1b. Masked destination flow
The masked destination flow allows users to specify a destination based on a generated identifier key corresponding to that destination, rather than submitting the destination directly. Before the MFA-setup OTP can be generated, the user’s destination addresses must be masked using the self-service "Get Masked User Identifiers" API:
Once the masked identifiers keys are created, an OTP must be generated and delivered to the destination (specified using the corresponding masked identifier key) using the self-service "Setup OTP MFA" API.
2. Confirming OTP setup
Once the OTP has been sent to the destination, the user must return it through the self-service "Confirm OTP MFA Setup" API, in order to verify the destination address. This step is performed in the same manner, regardless of whether the OTP was sent according to the explicit destination or masked destination flow.
Upon success, the email or mobile address is upgraded to "verified" status, and the user’s otpSetupComplete is set to true. An auth event may also be generated for the current session indicating that OTP setup is completed.
|
Tip
|
Configuration Tip: Automatic OTP authentication
Certain authorization policies may choose to treat the OTP setup auth event as equivalent to OTP authentication. This has the effect of allowing the user to skip re-authentication once setup is completed. |
OTP Authentication
Once OTP MFA setup is completed, the user may perform OTP authentication by receiving and successfully returning an OTP challenge.
1. Send OTP Challenge
The OTP challenge may be generated and sent according to the explicit destination flow, or through the masked destination flow.
1a. Explicit destination flow
To send the OTP challenge according to the explicit destination flow, the self-service "Send Authentication OTP" API must be called with a destination address and delivery mode specified:
1b. Implicit destination flow
To send the OTP challenge according to the implicit destination flow, the self-service "Send Authentication OTP" API must be called with an empty request body. The OTP will be generated and sent according to the user’s otpMfaDestination and otpMethod attributes.
1c. Masked destination flow
To to send the OTP challenge using a masked identifier, the self-service "Get Masked User Identifiers" API must have been called first. See API — Get Masked User Identifiers (Self-Service) for details.
Once the masked identifier has been generated, the self-service "Send Authentication OTP" API may be called:
Using the AuthN UI, an OTP MFA user may request an OTP challenge:
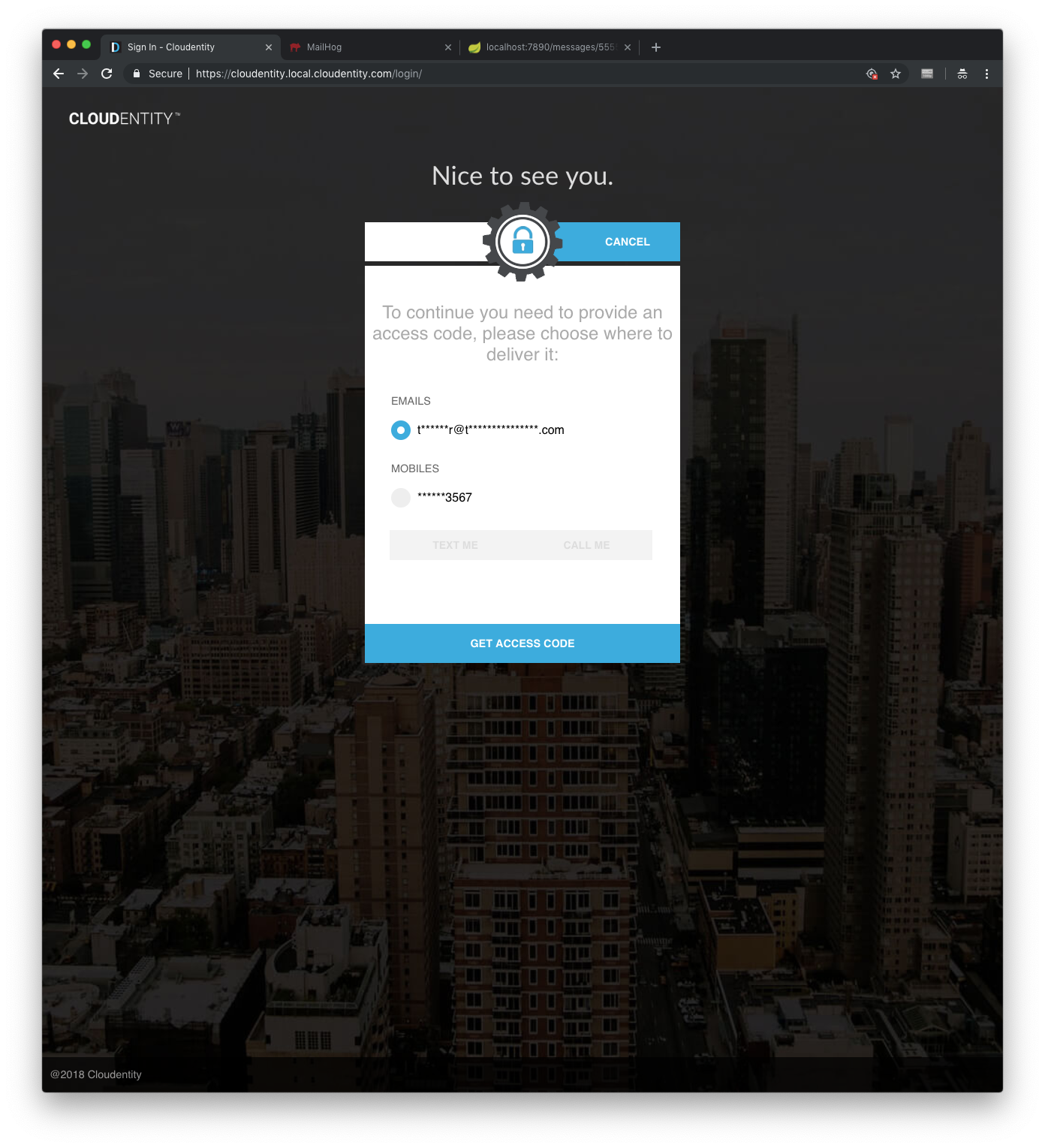
Once the OTP has been sent, the UI prompts for the OTP:
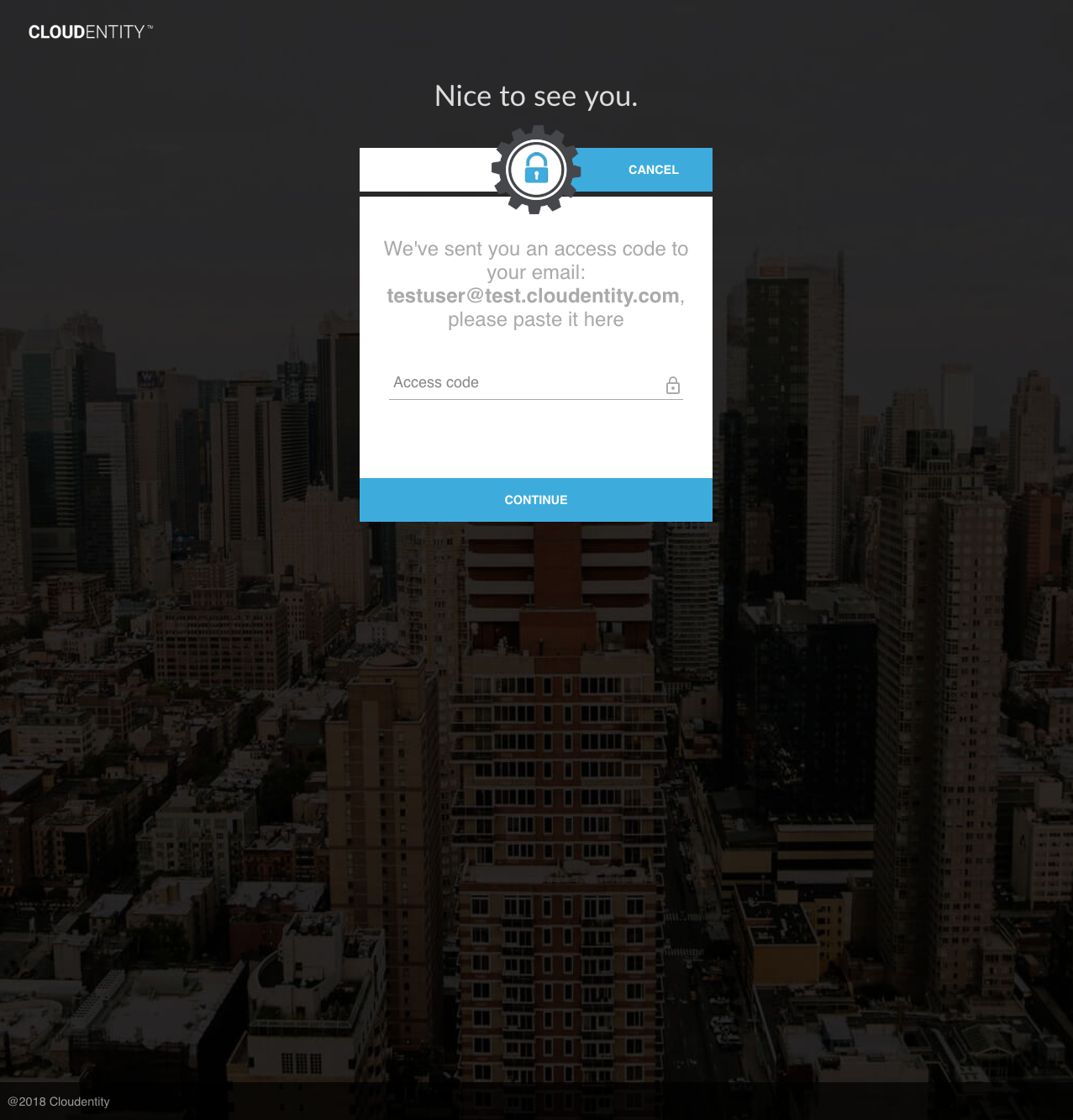
2. Complete OTP Authentication
2a. Retrieve OTP
The OTP value may be retrieved from an email, SMS message or voice message:
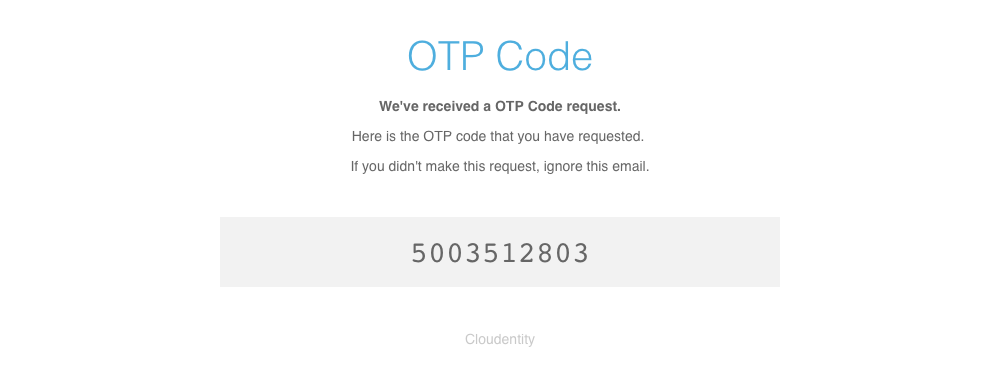
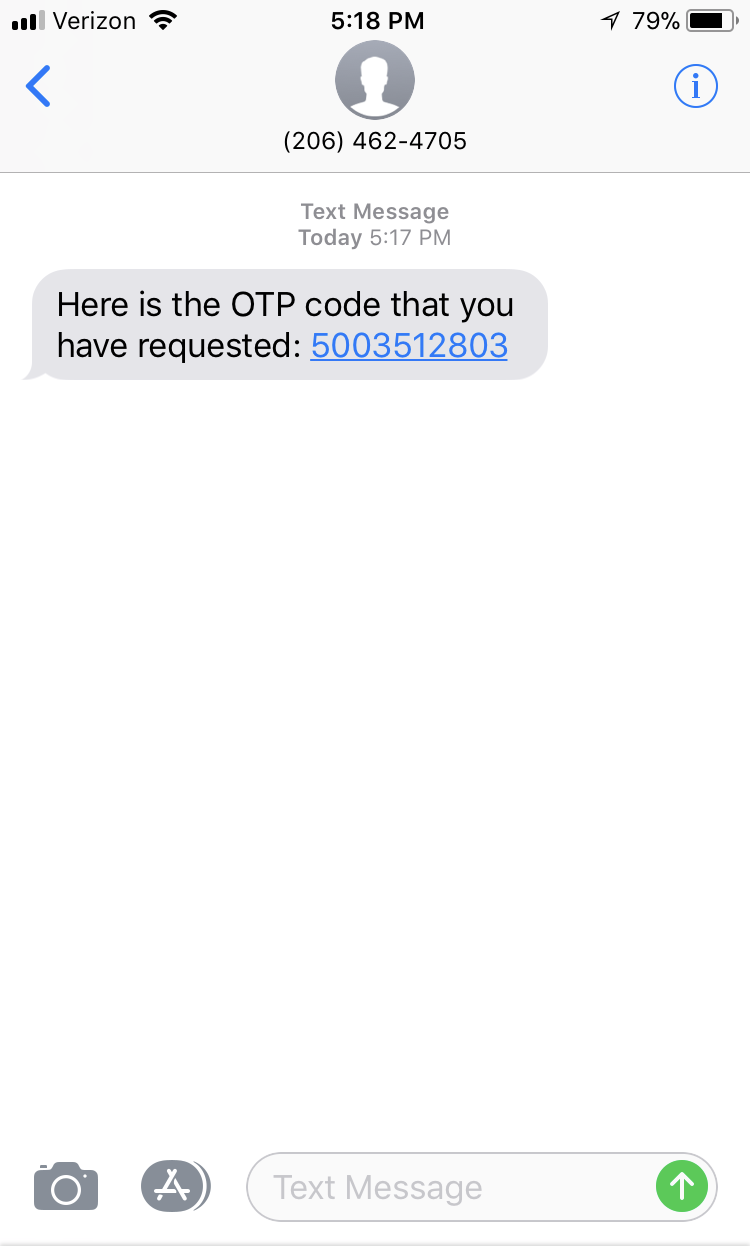
2b. Complete OTP Authentication
Once the OTP has been received, OTP authentication can be completed by calling the "OTP Authentication" API. This step is performed in the same manner, regardless of whether the OTP was sent according to the explicit destination, implicit destination or masked destination flow:
The OTP may also be submitted using the AuthN UI:
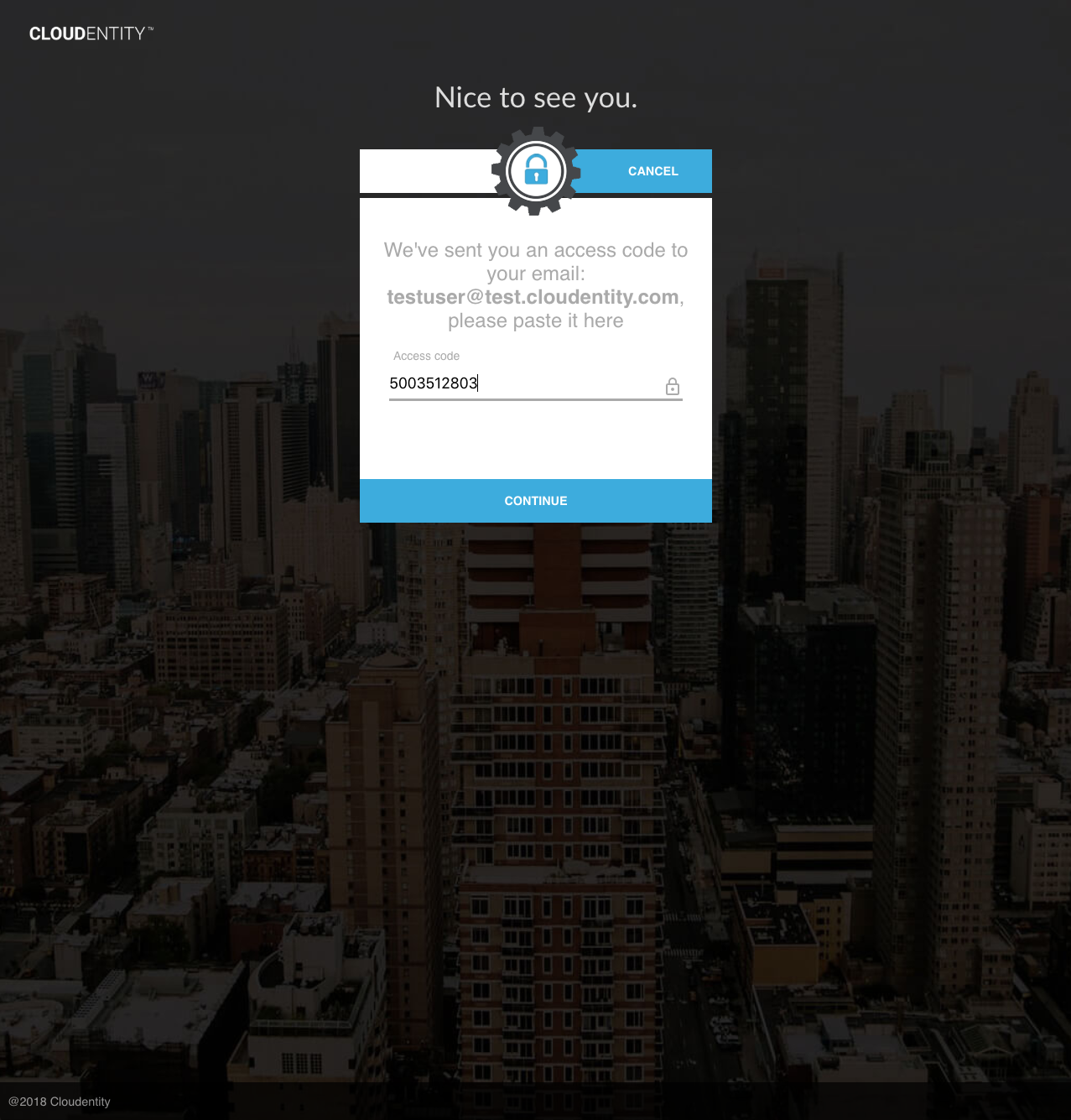
OTP Management
Reset OTP MFA Enrollment
In order to protect a user account whose credentials may have been compromised, it is possible to clear OTP MFA enrollment for a user. An administrative user may reset user’s otpMfaDestination, otpMethod and otpSetupComplete attributes using the administrative "Reset OTP MFA Enrollment" API:
Change OTP MFA Destination
Users who have completed OTP MFA enrollment can change their own default OTP destination. This flow begins by sending a verification OTP to the desired new address, using the self-service "Send Verification Code" API:
Once the OTP has been received, the update can be completed using the self-service "Change OTP MFA Destination" API:
Knowledge-Based Authentication (KBA)
Knowledge-Based Authentication (KBA) is achieved when a user correctly answers questions whose answers would only be known by the user. Examples of such questions include:
-
"In what city were you married?"
-
"In what city was your high school?"
When correct answers are submitted, the user’s identity is trusted.
|
Note
|
Relevant user attributes for KBA MFA:
|
KBA Global Config
The KBA system is governed by a global configuration object, which can be retrieved using the "Get KBA Config" API:
The KBA config attributes are used for the following purposes:
-
kbaConfigId: Unique identifier for this KBA config. Always has the value "default". -
kbaMinQuestionsPerUser: Minimum number of KBA questions to be answered by each user. -
kbaMaxQuestionsPerUser: Maximum number of KBA questions which may be stored by each user. -
kbaQuestionSet: Set of available questions which may be used for KBA.-
questionIdentifier: Unique identifier for a KBA question (most KBA APIs utilize this value). -
questionPhrase: Display phrase for a KBA question.
-
|
Warning
|
The global KBA configuration is initialized upon deployment of the Cloudentity Stack. No APIs are exposed to update the KBA configuration. |
KBA Setup
In order to set up KBA, the user must store personal responses to a set of questions. This can be done at user registration time (if using self-service "Register User" API), or with an authenticated session using the self-service "Set User KBA Responses" API:
|
Note
|
The number of responses the user provides may not exceed the global KBA config’s kbaMaxQuestionsPerUser, and may not be less than the kbaMinQuestionsPerUser.
|
The UI may be used to set KBA responses at registration time. If the user selects "Knowledge-based Authentication" for MFA Method, the user will be prompted to supply KBA responses:
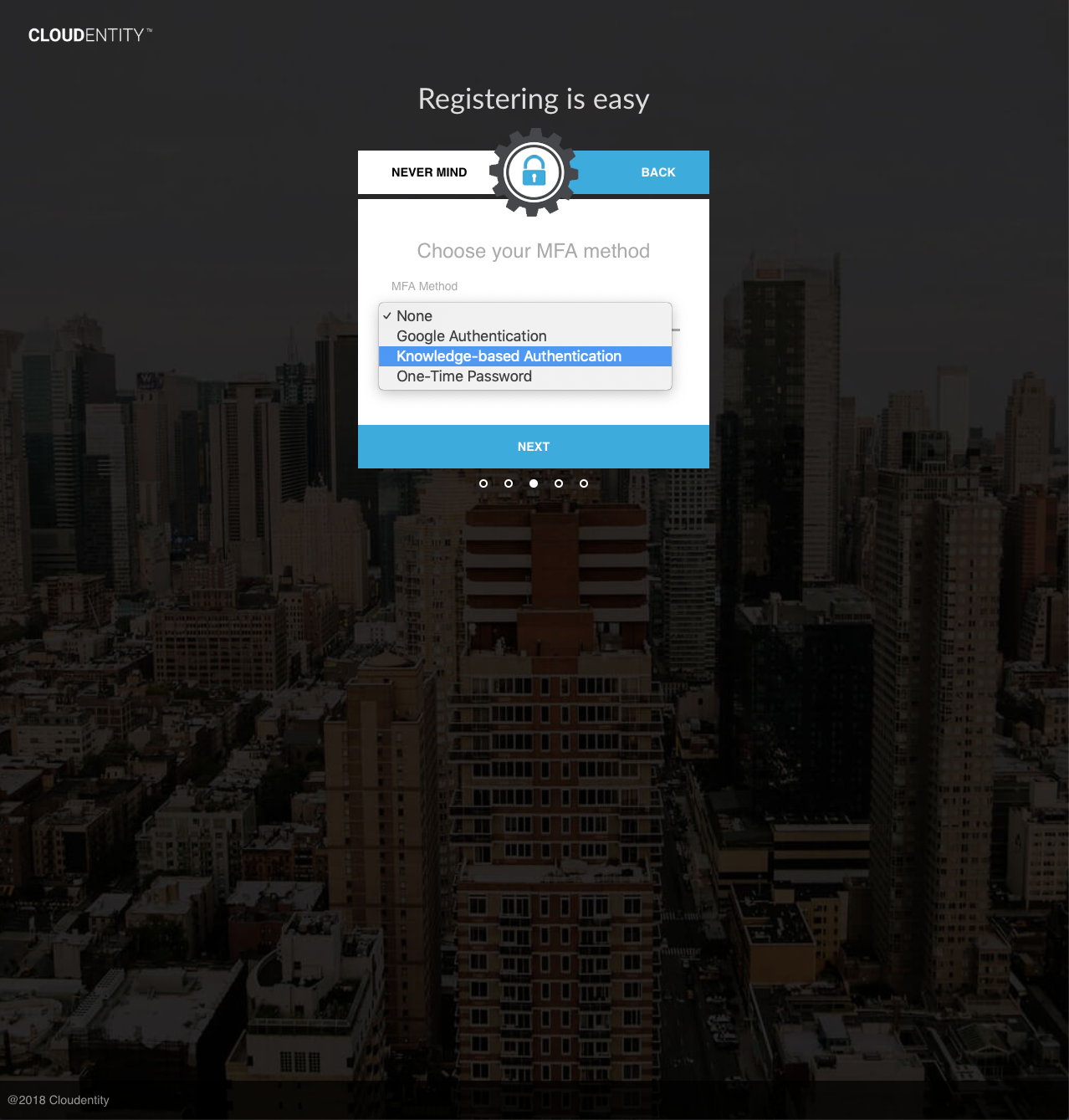
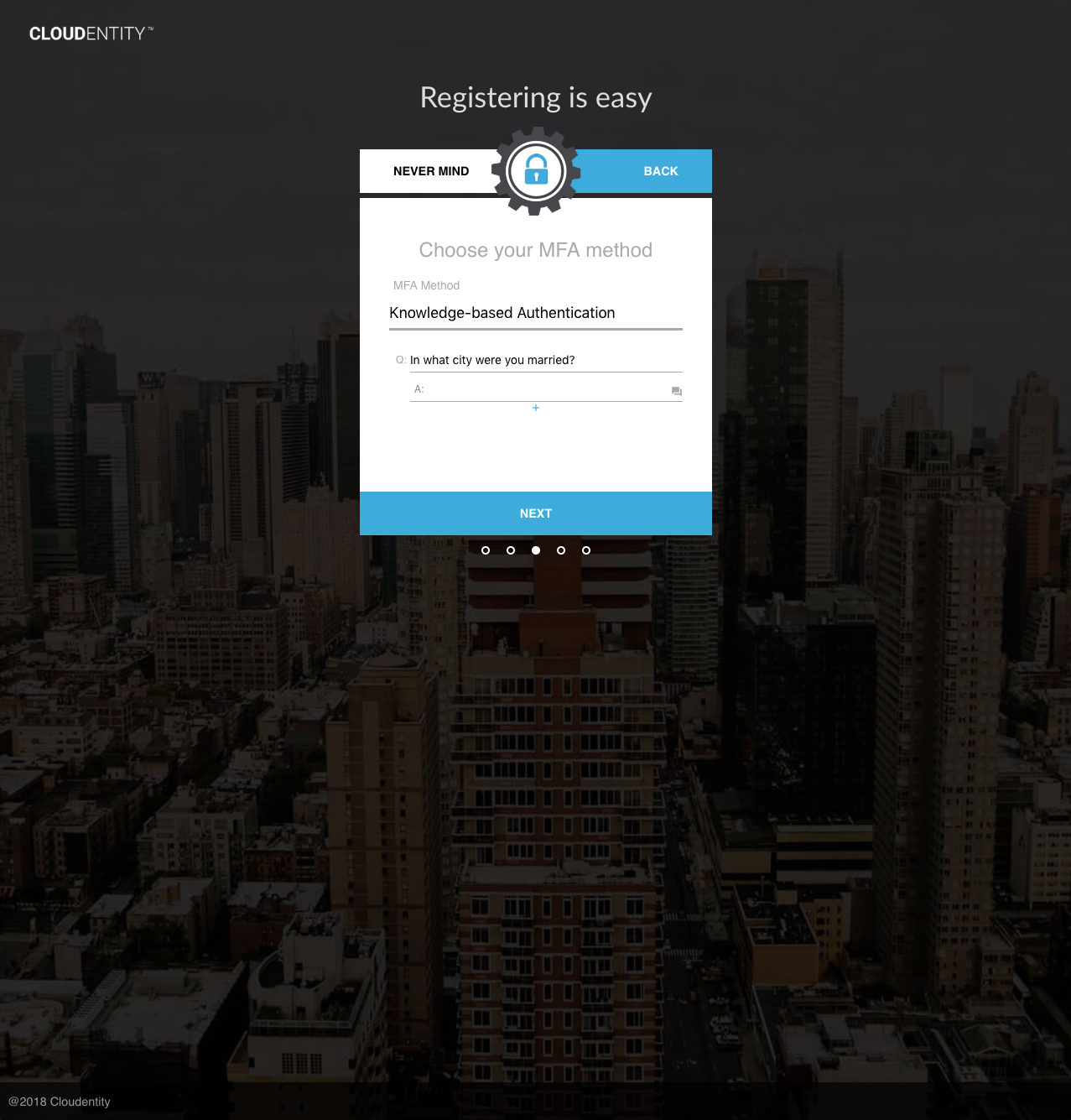
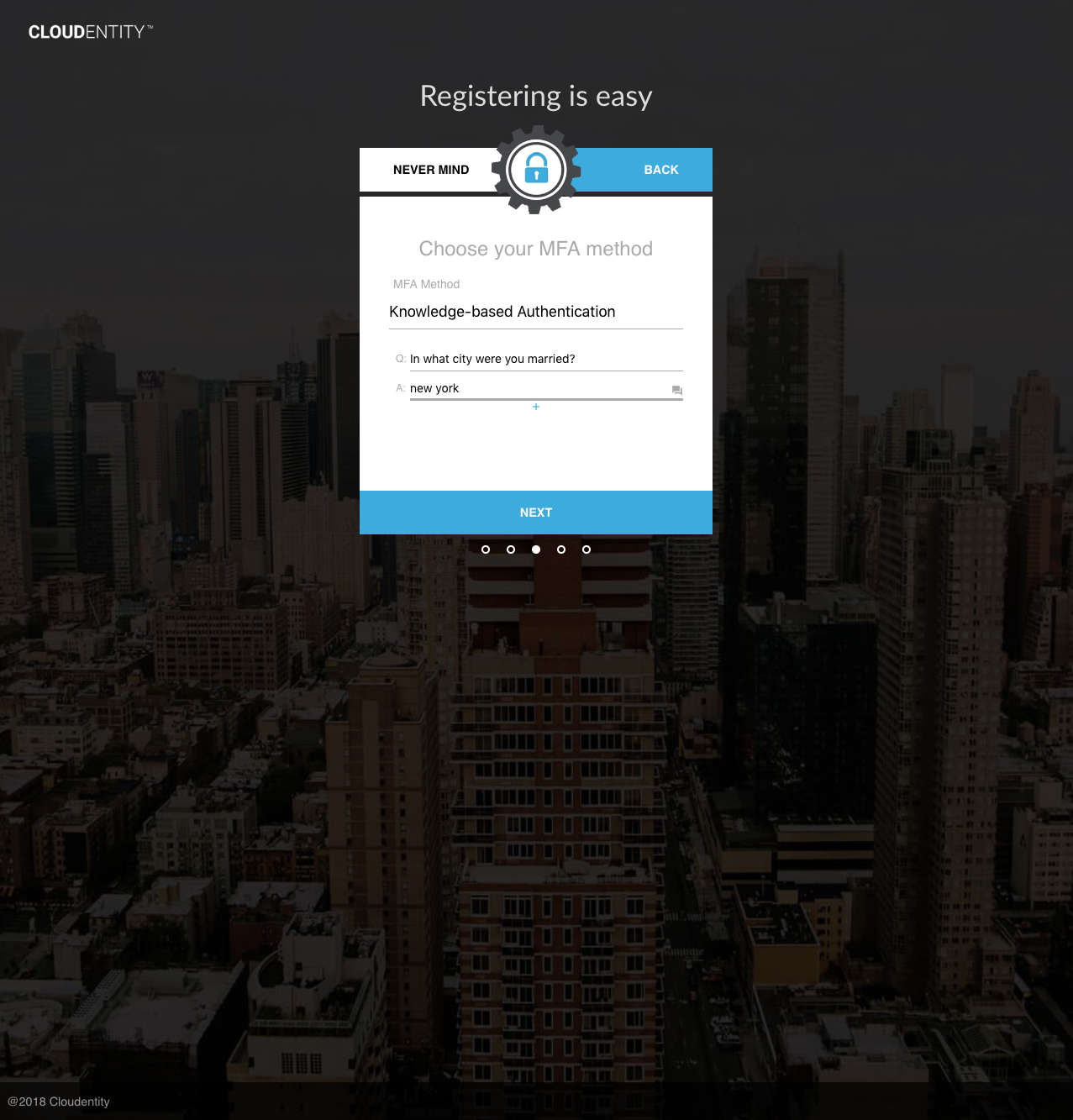
Upon success of any of the above methods, the user’s responses will be hashed and stored in the user’s kbaResponseSet attribute. Any existing kbaPendingQuestions (i.e. from past authentications) will be cleared.
KBA Authentication
Once the user’s KBA responses are set up, the user can proceed to authentication.
1. KBA Challenge
The user must generate a set of challenge questions to answer by calling the self-service "Generate User KBA Challenge" API:
|
Note
|
The UI will automatically call this API when a KBA-enabled user completes their first-factor authentication. |
Upon success, the challenge questions are stored in the user’s kbaPendingQuestions attribute. Until the user completes authentication or the KBA challenge is cleared, successive calls to generate a KBA challenge will yield the same question set.
|
Note
|
The global KBA config’s |
2. KBA Authentication
Once a KBA challenge is generated, the user must respond to exactly this set of questions for authentication to succeed.
The UI displays the KBA challenge view:
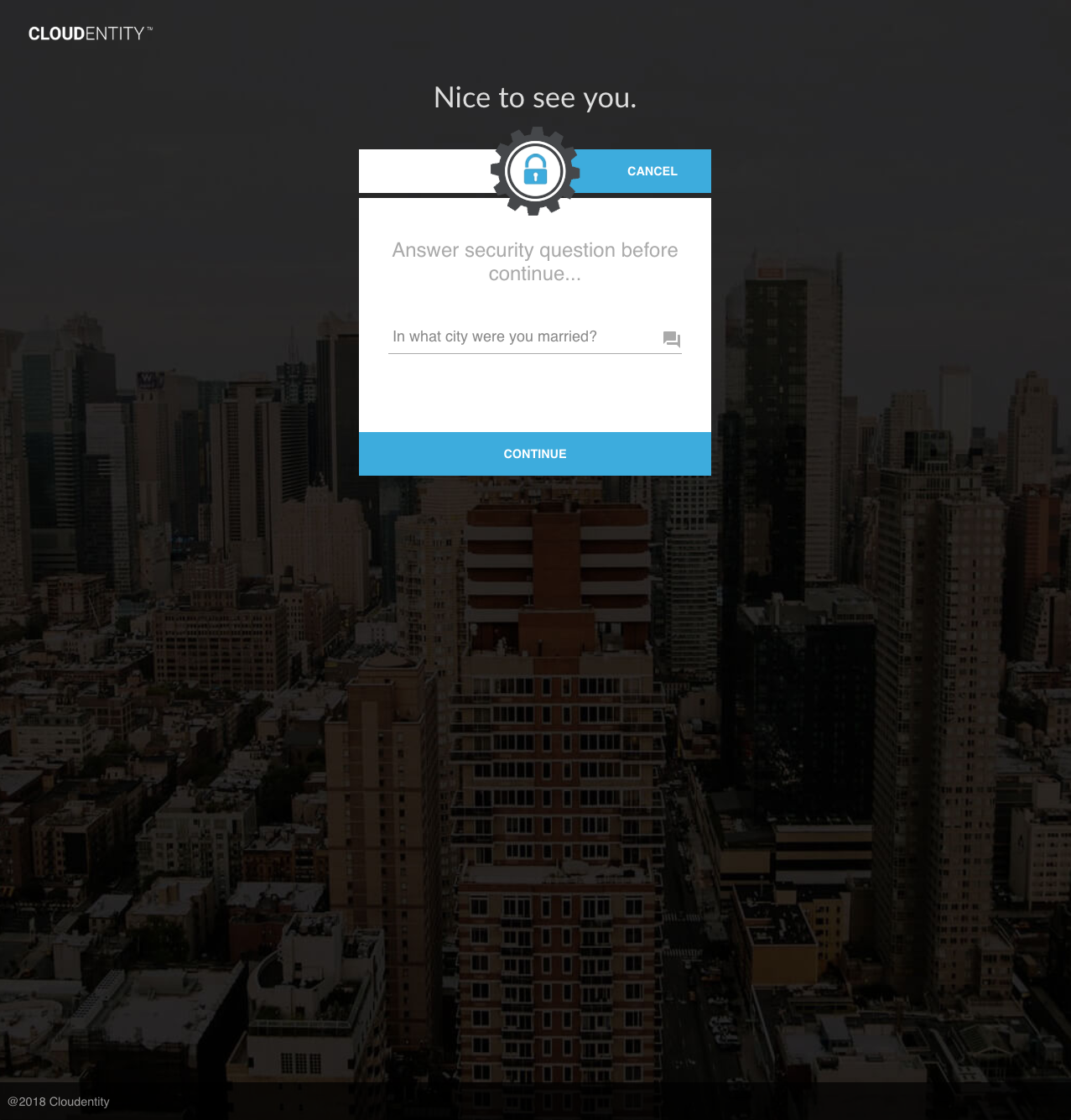
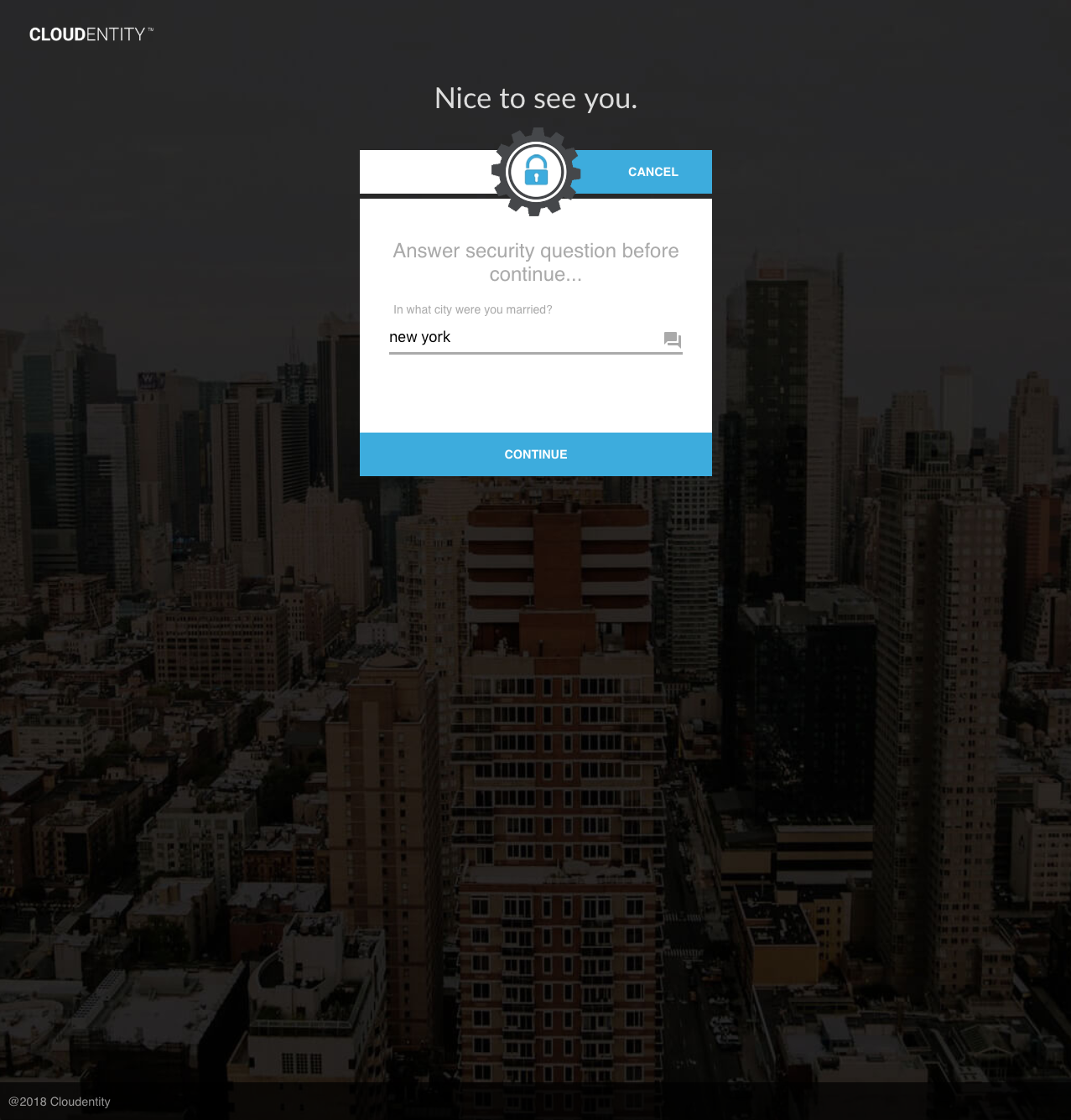
Upon success, a KBA Authentication auth event is generated for the current session. Authorization policies which require this event will pass for this session.
KBA Management
In order to protect a user account whose KBA answers may have been compromised, an admin can reset the user’s KBA responses using the "Reset User KBA" API:
Upon success, the user’s kbaResponseSet is cleared, forcing the user to set up KBA responses again. Any existing challenge questions for the user are also cleared.
Supplementary Features
Preferred MFA Method
A user attribute, mfaMethod, is available to specify the user’s preferred means of MFA. Authorization policies may utilize this attribute to direct a user through an MFA flow. Authenticated users may update their mfaMethod using the self-service "Set MFA Method" API:
Reset MFA Credentials
This flow provides a reset path to a user who has forgotten an MFA credential.
An administrative user sends a verification OTP or encrypted code to a user to reset MFA for a specific type. Verification of the code partially authenticates the user, enabling further action based on authorization policy configuration.
The flow begins with an admin calling the "Request Reset MFA Credentials" API, providing a specific MFA type for which this reset is valid. The provided destination must be among the target user’s email or mobile addresses.
Once the verification OTP or encrypted code is received, the user may call the "Verify Reset MFA Credentials" API:
The session generated by this API is granted an auth event specific to that MFA type. Policies may use these auth events to allow users access to additional, alternative-login resources.