1. SAML IdP Overview
Cloudentity SAML IdP services facilitates exchange of authentication and authorization information across different organizations with different security domains.
SAML is an XML based language to exchange security assertions. SAML defines following actors:
-
principal ⇒ end user trying to access a resource.
-
service provider ⇒ web resource that the principal is trying to access.
-
identity provider ⇒ server that holds the principal’s identities and credentials.
In this service, Cloudentity acts as the identity provider to generate SAML assertion responses and provide it to any trusted SAML service providers.
2. SAML Profile
One of the most widely used SAML profiles is Web Browser SSO Profile. Cloudentity IdP services supports both variants of the Web Browser SSO Profile
-
SP-Initiated SSO
-
"IdP-initiated" or "Unsolicited" SSO.
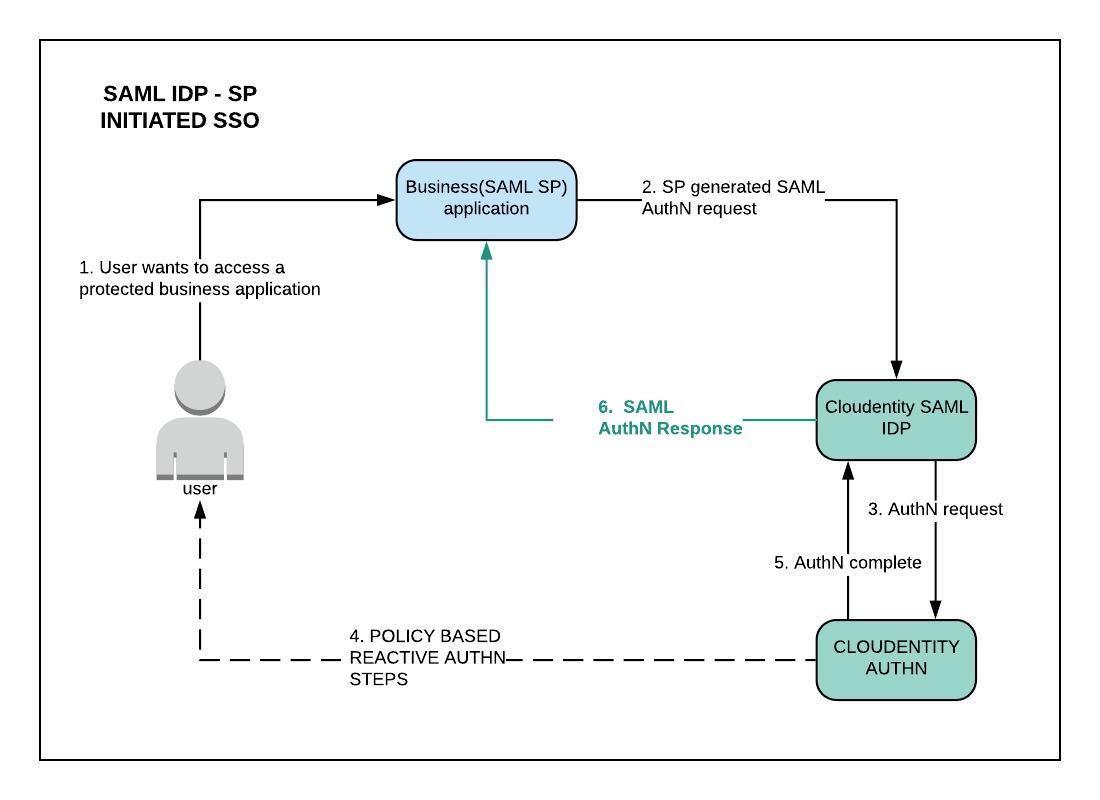
2.1. SP-initiated SSO
In SP-initiated SSO, the user attempts to access a resource on the SP. However they do not have a current logon session on this site and their federated identity is managed by their IdP. They are sent to the IdP to log on and the IdP provides a SAML web SSO assertion for the user’s federated identity back to the SP.
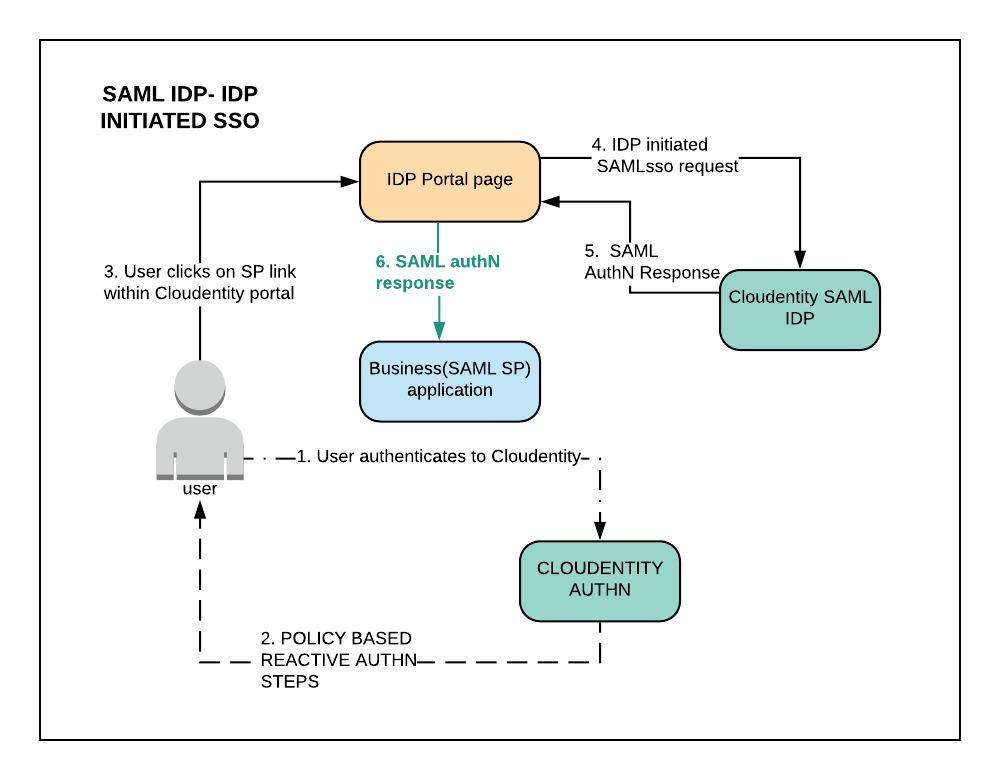
2.2. IdP-initiated SSO
In an IdP-initiated use case, the identity provider is configured with specialized links that refer to the desired service providers. These links actually refer to the local IdP’s Single Sign-On Service and pass parameters to the service identifying the remote SP. So instead of visiting the SP directly, the user accesses the IdP site and clicks on one of the links to gain access to the remote SP. This triggers the creation of a SAML assertion that will be transported to the service provider using the HTTP POST binding.
3. Configuration
Following steps need to be done to set up Cloudentity as external IdP for any SAML Service Provider.
3.1. Steps
-
Get SAML Metadata from Cloudentity IDP. Learn more
-
IdP SAML metadata (SAML)
-
IdP Certificate
-
-
Register Cloudentity as Identity Provider in SAML Service provider
-
Follow steps provided by your SAML service provider to complete this
-
-
Download SAML metadata from external SAML service provider
-
Follow steps provided by your SAML service provider to complete this.
-
-
Register external SAML service provider within Cloudentity. Learn more
-
Verify Single Sign On via either SP initiated or Idp initiated sso mechanisms. Learn more
|
Note
|
Above outlined workflow is the default workflow. Workflows and redirects may be modified per Identity Provider configuration, using advanced settings within Cloudentity system based on custom business requirements. |
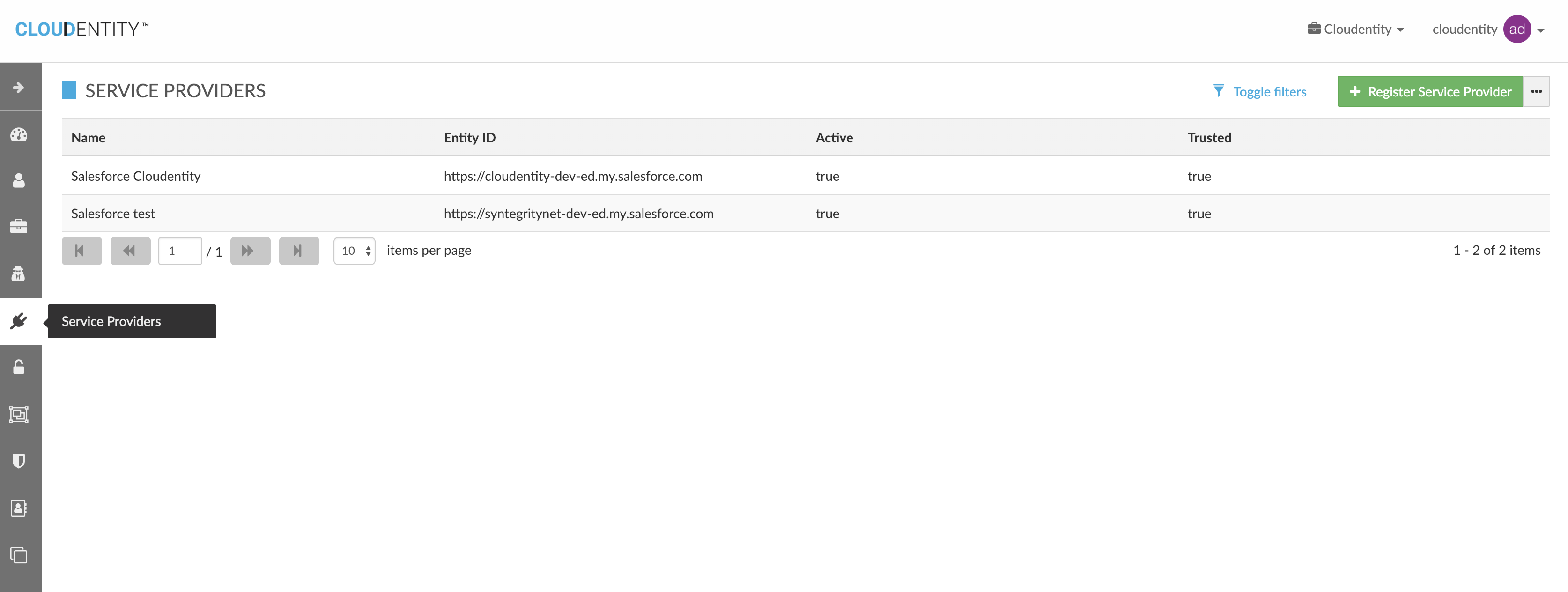
3.2. Federation Management Admin User Interface
Cloudentity administrative UI application provides a simple user interface to manage external third party SAML service provider agreement and mapping information. Administrative users need to have proper entitlement to act on specific actions. Each of these actions in UI are mapped directly to specific entitlements for user to allow fine grained access control of these operation from an administrative panel.
-
List Service Providers
-
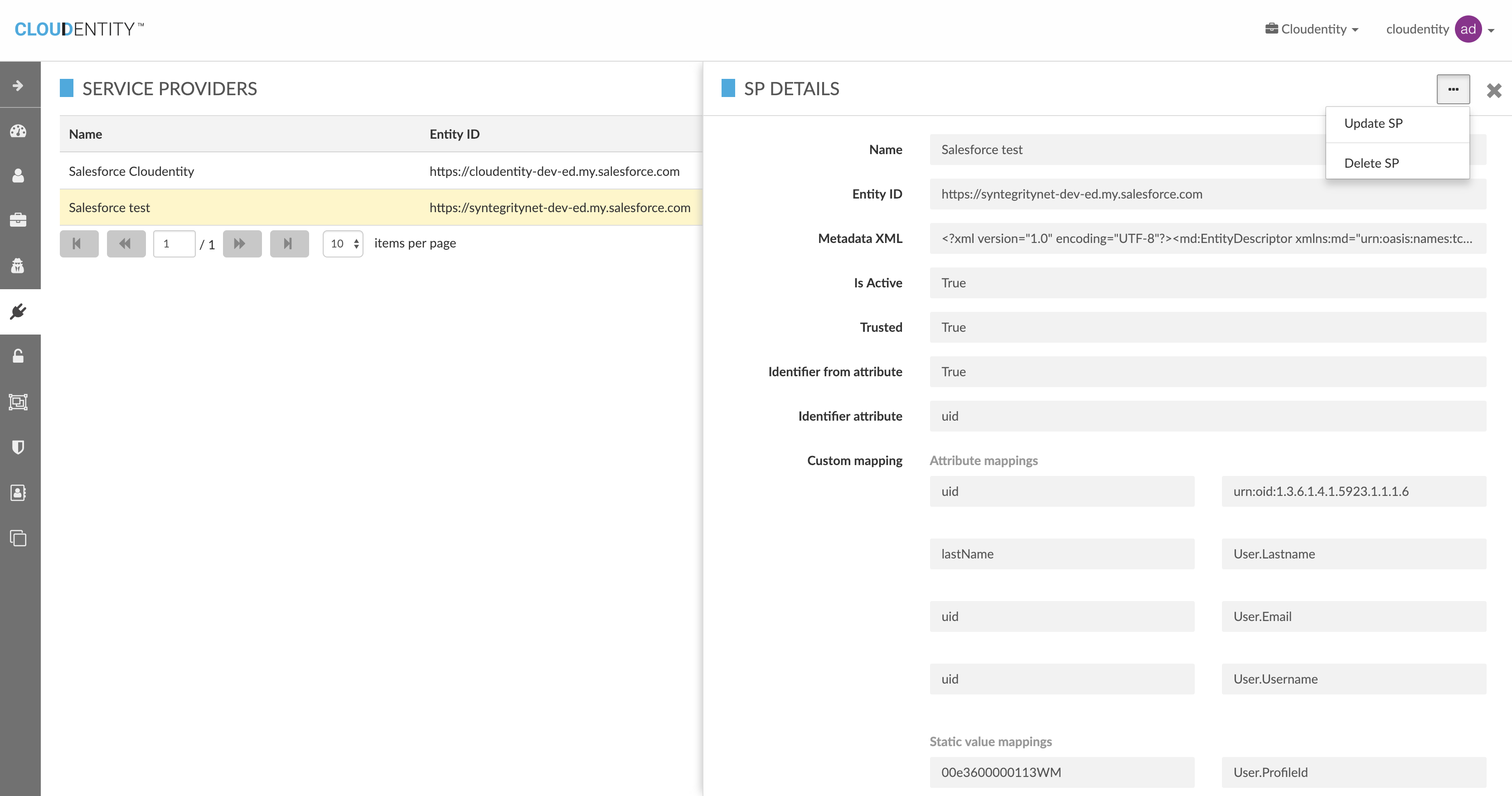
Get Service Provider
-
Register Service Provider
-
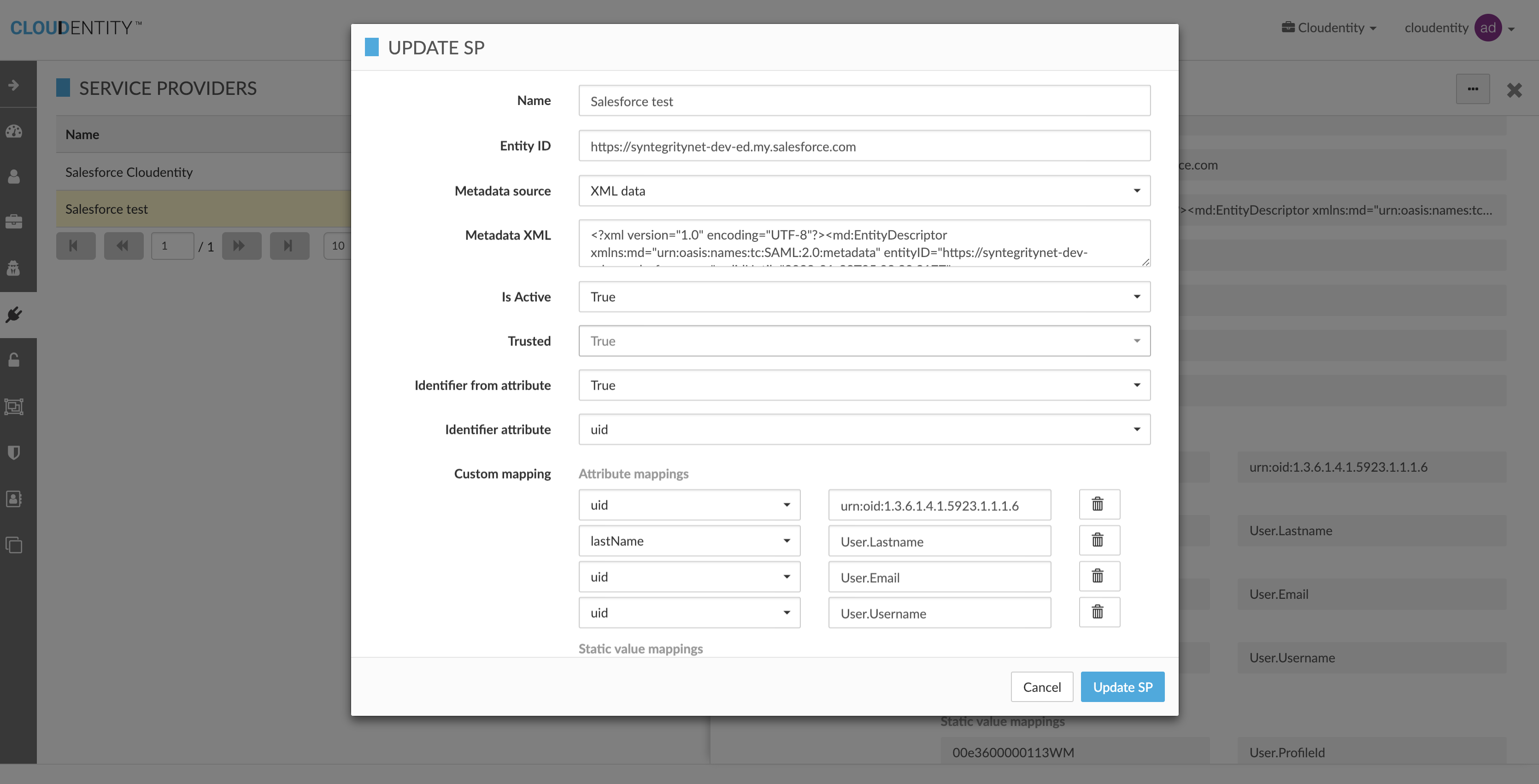
Update Service Provider
-
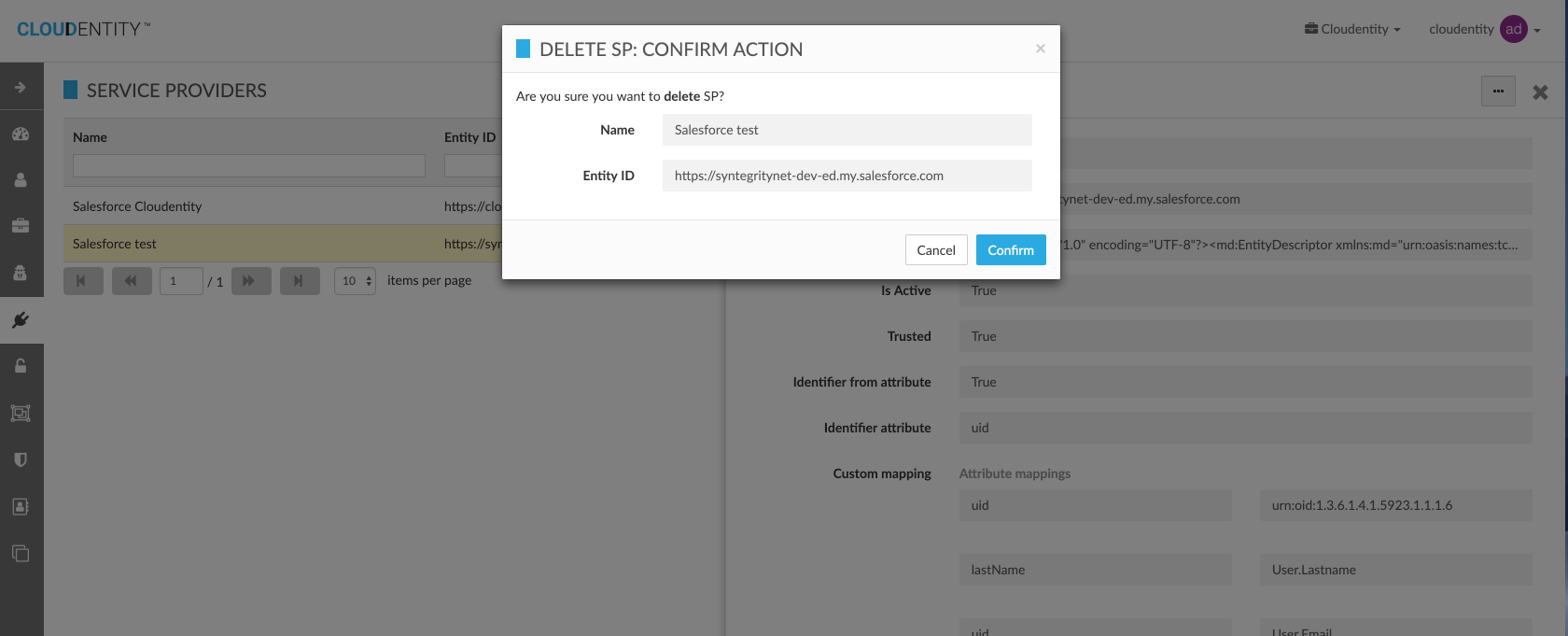
Delete Service Provider
List Service Providers
Get Service Provider
|
Note
|
Register SAML as Identity Provider |
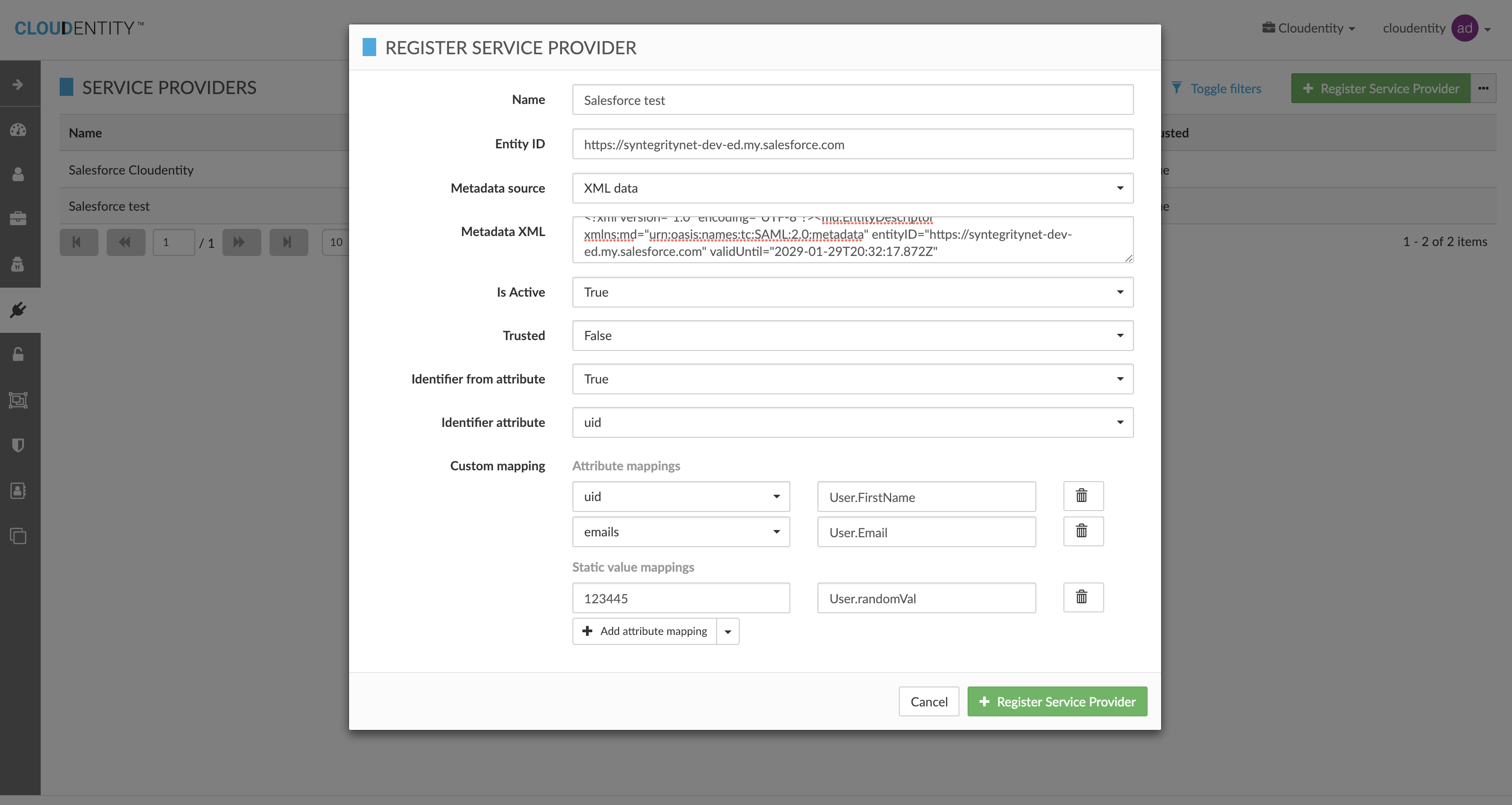
Register Service Provider
Update Service Provider
Delete Service Provider
3.3. Download Cloudentity IdP SAML Metadata
Cloudentity SAML metadata information has to be provided to SAML Service Provider for registering Cloudentity as Identity Provider.
Cloudentity metadata can be downloaded from Cloudentity System either via:
-
Administrative UI
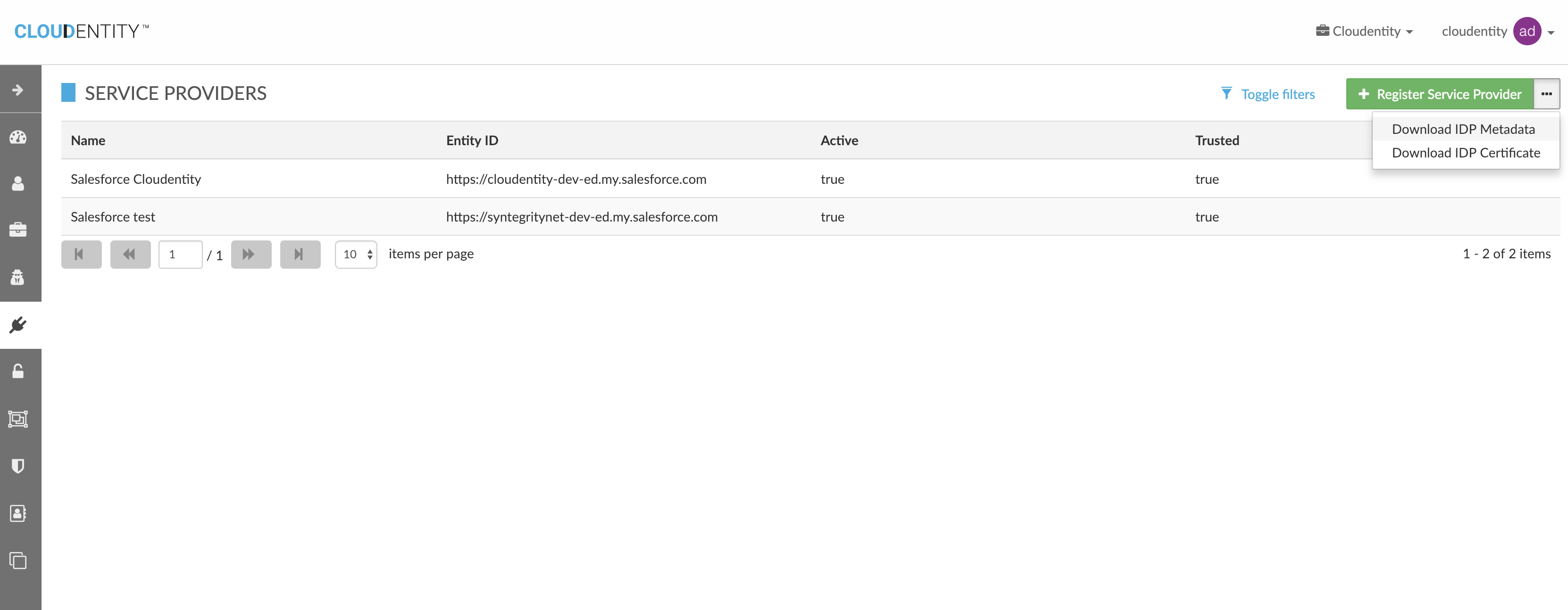
-
API Call
-
Get IdP Metadata
-
GET https://<cloudentity-saml-idp-host>/saml/metadata-
Get IdP Certificate
GET https://<cloudentity-saml-idp-host>/saml/certificate3.3.1. Sample metadata
<?xml version="1.0" encoding="UTF-8"?>
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:mdui="urn:oasis:names:tc:SAML:metadata:ui" xmlns:shibmd="urn:mace:shibboleth:metadata:1.0" entityID="https://ecs.cylance.cloudentity.com/saml">
<IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol urn:oasis:names:tc:SAML:1.1:protocol urn:mace:shibboleth:1.0">
<Extensions>
<shibmd:Scope regexp="false">ecs.cylance.cloudentity.com</shibmd:Scope>
</Extensions>
<KeyDescriptor>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>REPLACE_WITH_CLOUDENTITY_IDP_X509_CERTIFICATE</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes128-gcm" />
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes192-gcm" />
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes256-gcm" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#rsa-oaep" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p" />
</KeyDescriptor>
<ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:1.0:bindings:SOAP-binding" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML1/SOAP/ArtifactResolution" index="1" />
<ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/SOAP/ArtifactResolution" index="2" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/Redirect/SLO" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/POST/SLO" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/POST-SimpleSign/SLO" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/SOAP/SLO" />
<NameIDFormat>urn:mace:shibboleth:1.0:nameIdentifier</NameIDFormat>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>
<SingleSignOnService Binding="urn:mace:shibboleth:1.0:profiles:AuthnRequest" Location="https://ecs.cylance.cloudentity.com/saml/profile/Shibboleth/SSO" />
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/POST/SSO" />
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/POST-SimpleSign/SSO" />
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/Redirect/SSO" />
</IDPSSODescriptor>
<AttributeAuthorityDescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:1.1:protocol">
<Extensions>
<shibmd:Scope regexp="false">ecs.cylance.cloudentity.com</shibmd:Scope>
</Extensions>
<AttributeService Binding="urn:oasis:names:tc:SAML:1.0:bindings:SOAP-binding" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML1/SOAP/AttributeQuery" />
<!-- <AttributeService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://ecs.cylance.cloudentity.com/saml/profile/SAML2/SOAP/AttributeQuery"/> -->
<!-- If you uncomment the above you should add urn:oasis:names:tc:SAML:2.0:protocol to the protocolSupportEnumeration above -->
</AttributeAuthorityDescriptor>
</EntityDescriptor>3.3.1.1. SAML Metadata terms
| Name | Description |
|---|---|
EntityID |
Unique name representing a party in federation agreement |
NameIDFormat |
Format of the attribute for NameID in SAML response assertion |
SingleSignOnService Url |
SAML assertion producer endpoint after login. This value can be found within the Location block of SingleSignOnService |
3.4. Verify SAML Authentication flow
-
Initiate Cloudentity IdP authentication process either from Service Provider website or from IdP hosted website. Learn more about these flows at - SAML flows
-
SP Initiated SSO
Navigate to SP website and start authentication process.
-
IdP Initiated SSO
-
Navigate to IdP portal page and click on url that redirects to SP website OR launch below URL with your registered SP entity Id.
GET
https://<cloudentity-saml-idp-host>/saml/profile/SAML2/Unsolicited/SSO?providerId=<saml-sp-entity-id>example
GET https://ecs.cloudentity.com/saml/profile/SAML2/Unsolicited/SSO?providerId=https%3A%2F%2Fsyntegritynet-dev-ed.my.salesforce.com
-
User will be redirected to Cloudentity IdP to complete authentication process and on completion, user will be by redirected to external Service Provider page.
3.5. SAML Debugging tools
There are several SAML browser tools available to trace SAML assertions for federations based on SAML.
Firefox:
Chrome
4. SAML Integration Examples
4.1. Salesforce
Salesforce can be configured to authenticate with Cloudentity as single sign-on (SSO) identity provider , allowing end users to easily and securely access Salesforce.
Below steps are for guidance reference and latest Salesforce documentation must be followed to complete below setup
-
Fetch Cloudentity SAML metadata & IdP certificate
-
Login to Salesforce and set up a new SAML Single Sign On under Security Controls, if a setup does not already exist for the IDP
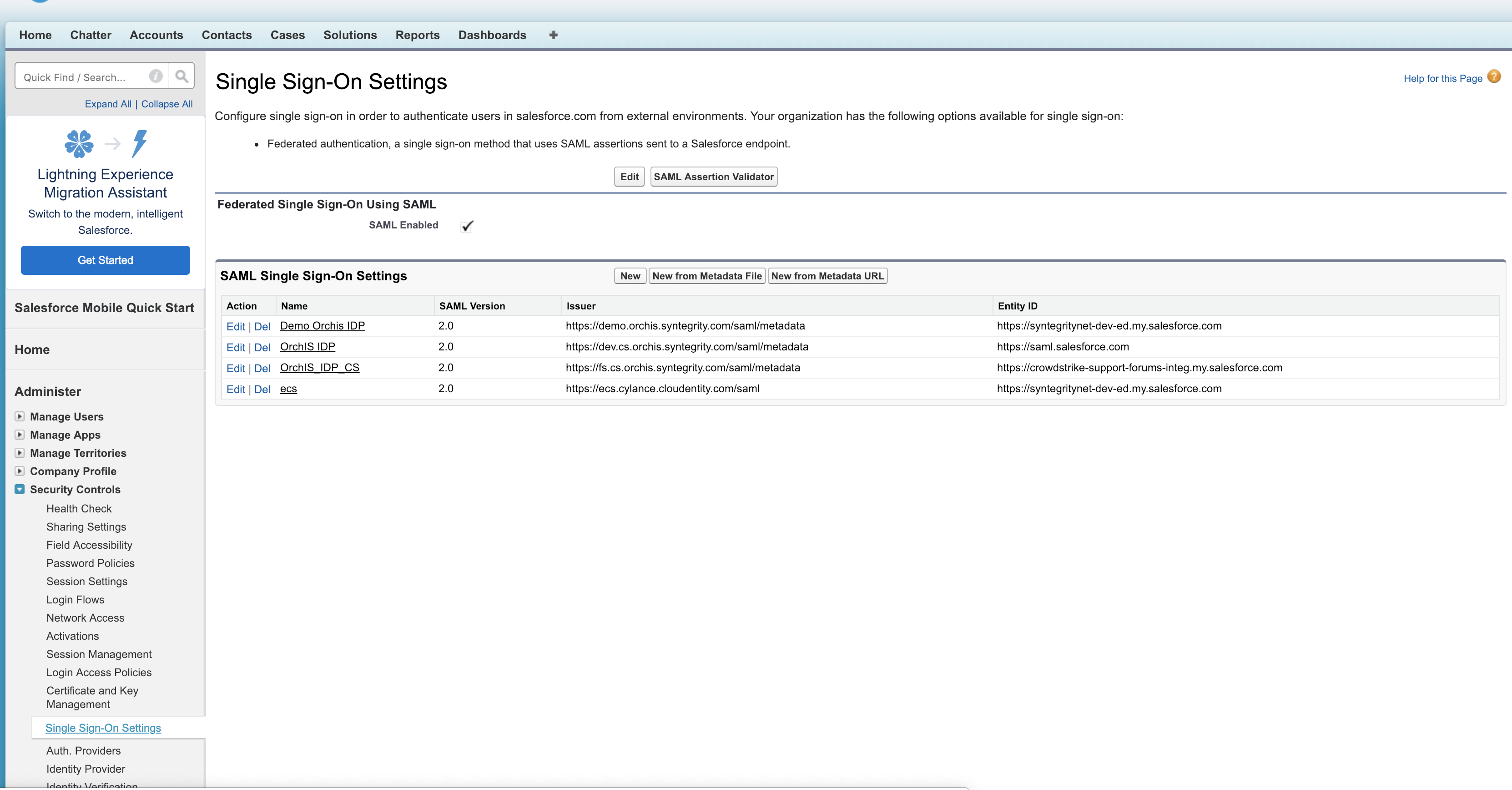
-
Upload Cloudentity Metadata and set up Salesforce for consuming SAML assertions, JIT etc
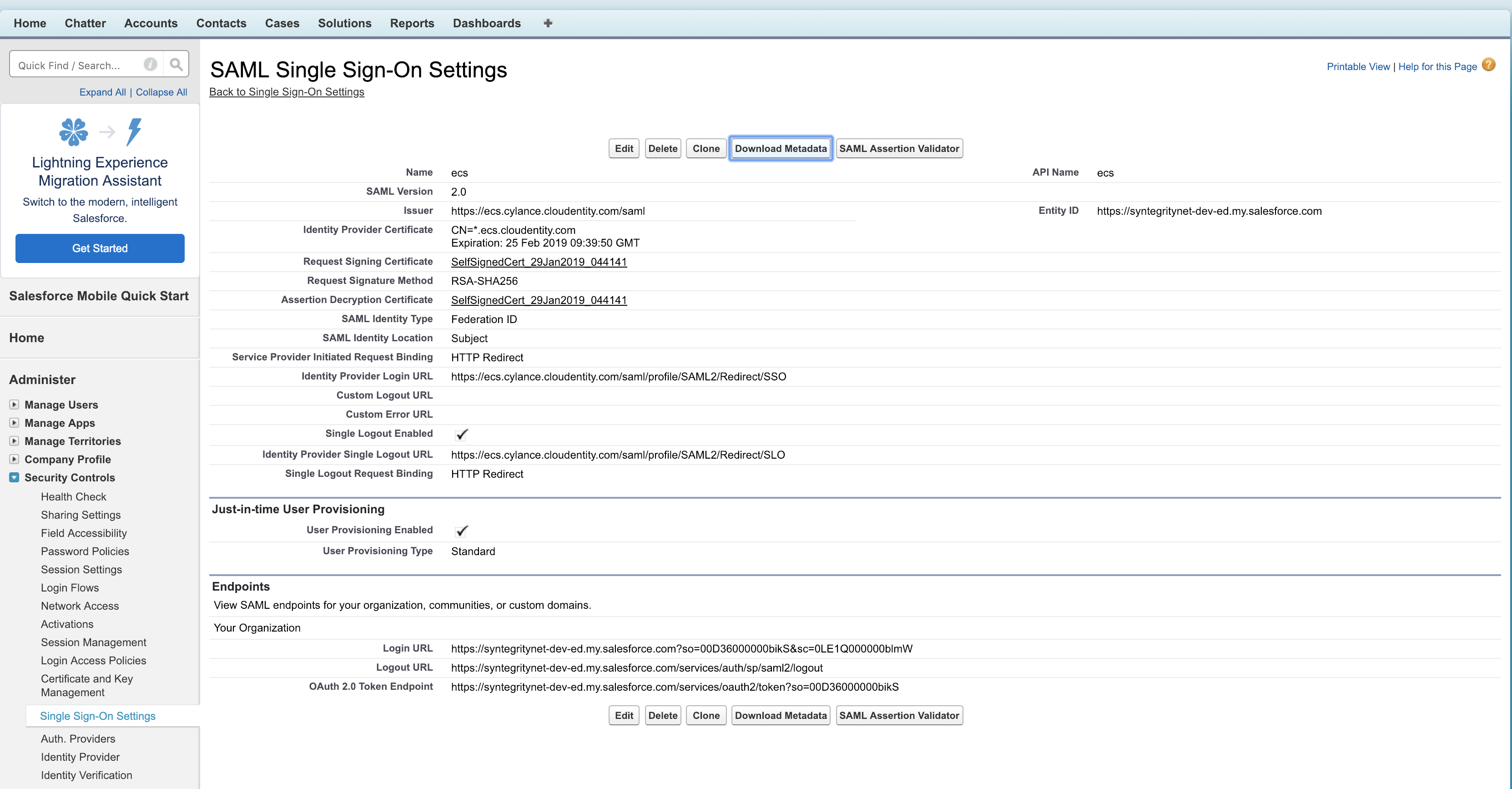
|
Note
|
Based on location SAML Identity Type & Location, registration mapping within Cloudentity should be adjusted as well. |
-
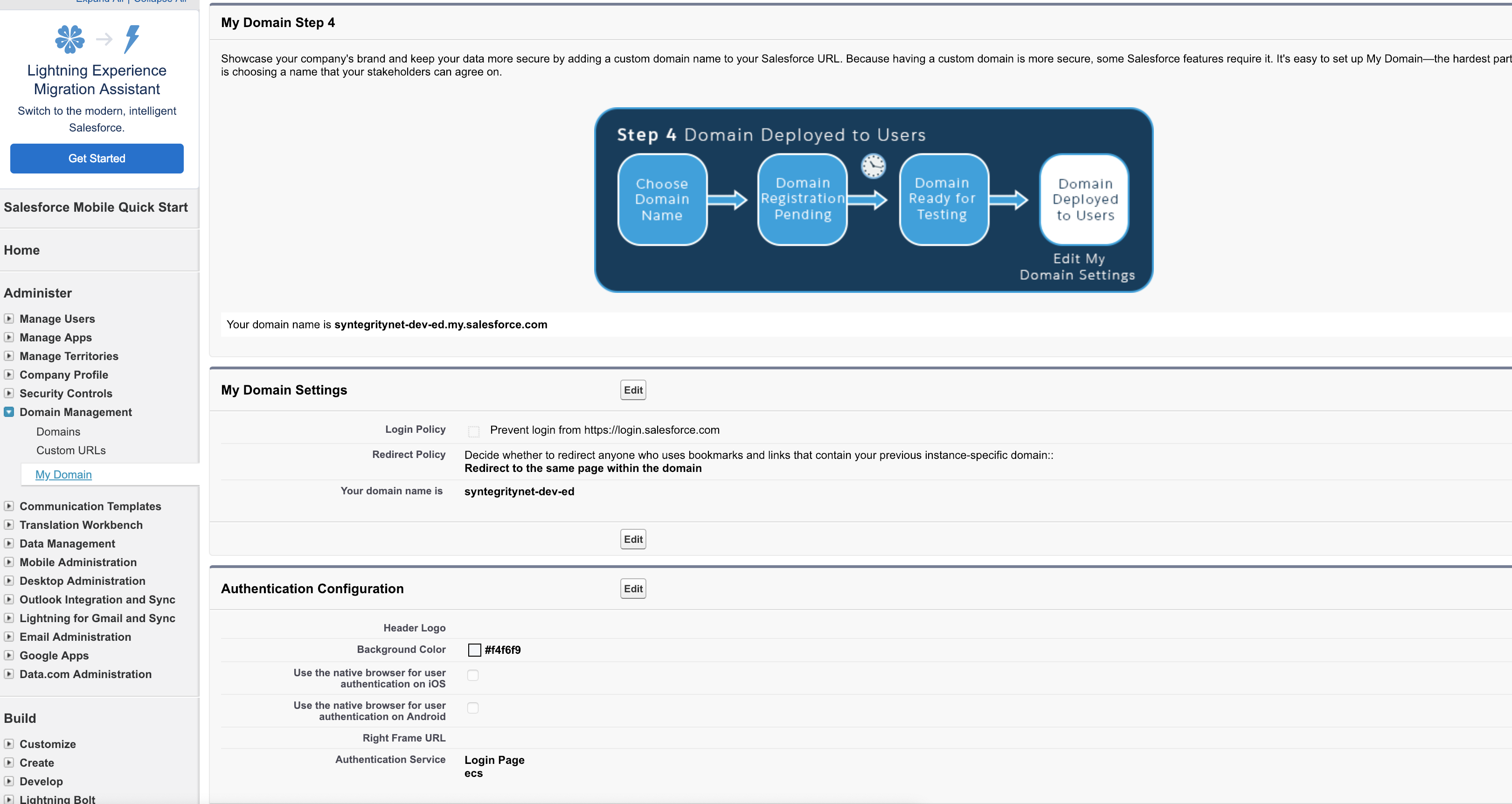
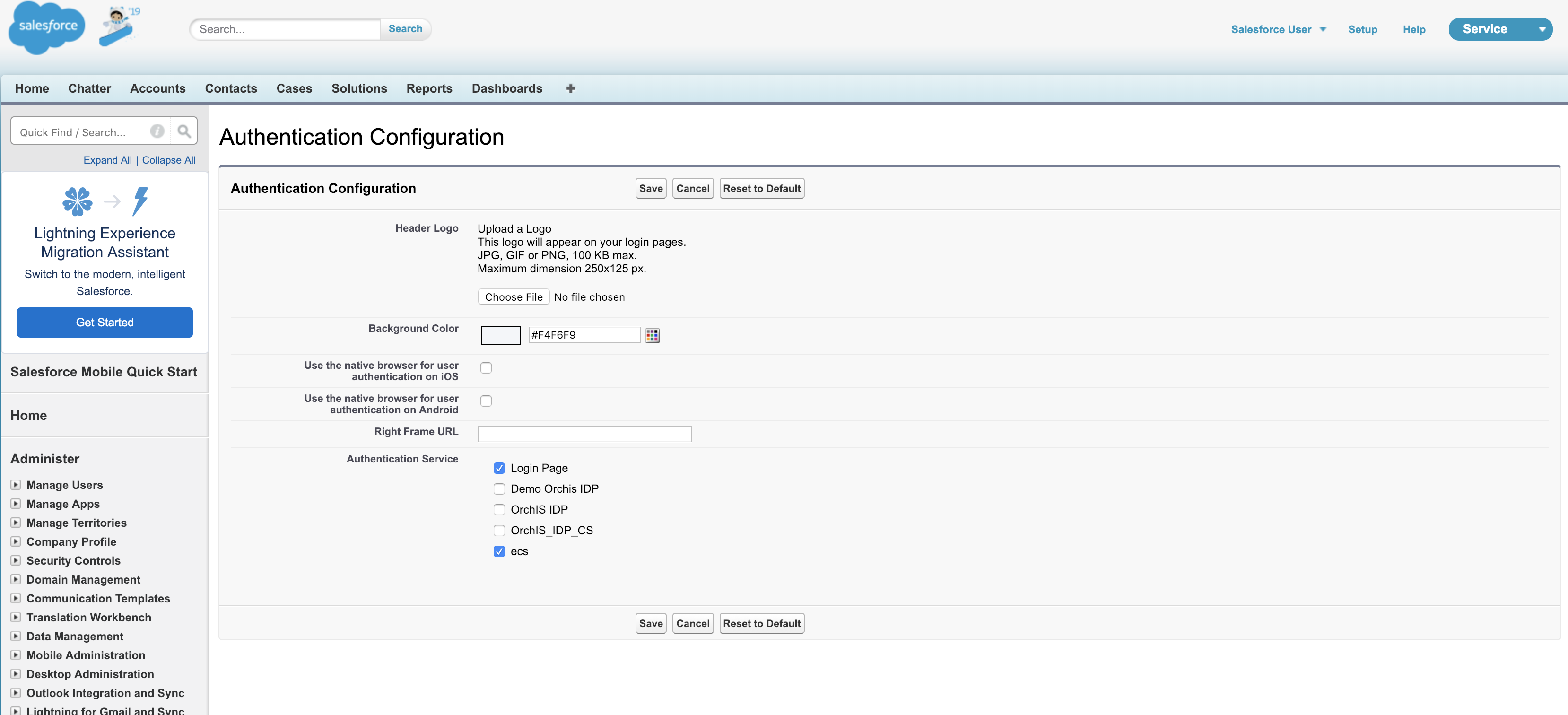
Configure Salesforce domain settings to allow the newly set up IdP as one of the authentication mechanisms
|
Note
|
After this is setup, the selected Identity Providers will be available in Salesforce login page as supported authentication providers |
-
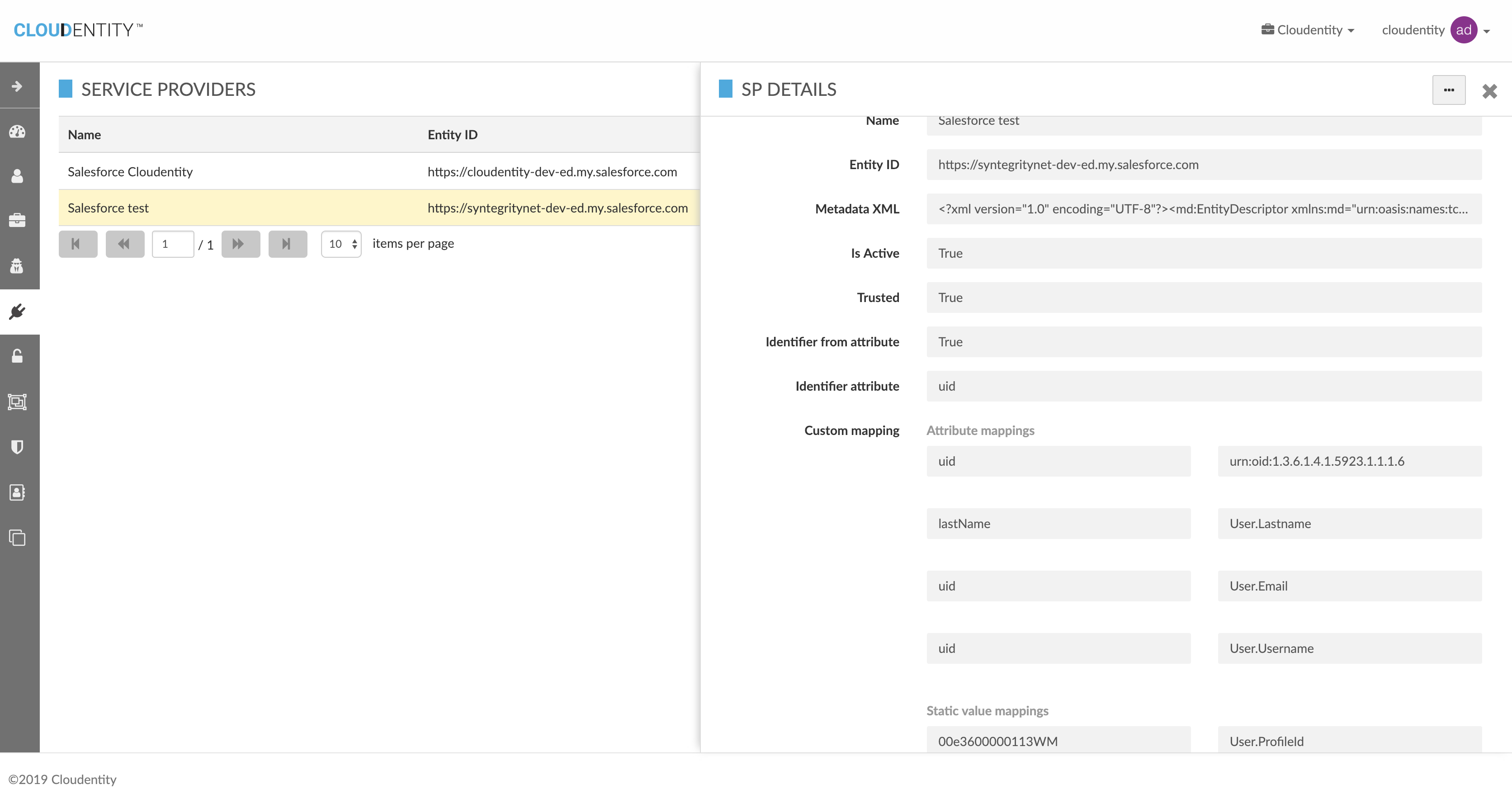
Register Salesforce as an SAML SP in Cloudentity Learn more
|
Note
|
Mappings are important based on organization’s preference on how to map user & profile attributes.If JIT is not enabled, its critical that the salesforce user information can be matched up based on the mapping in SAML assertion |
| Cloudentity Field Name | Salesforce Field Name | Data Source |
|---|---|---|
defaultEmail |
User.Email |
Session |
firstName |
User.FirstName |
Session |
lastName |
User.LastName |
Session |
lastName |
User.ProfileId |
Static |
|
Note
|
Identifier from attribute must be set to true if NameID needs to be released and set in SAML response assertion
Identifier attribute defines the authenticated session attribute that will be used to set the value of NameID
|
-
Verify authentication using either
-
SP initiated SSO
-
Idp initiated SSO
-
4.1.1. Troubleshooting
Salesforce related errors: