Introduction
Application Service stores information about applications and exposes set of APIs to manage them.
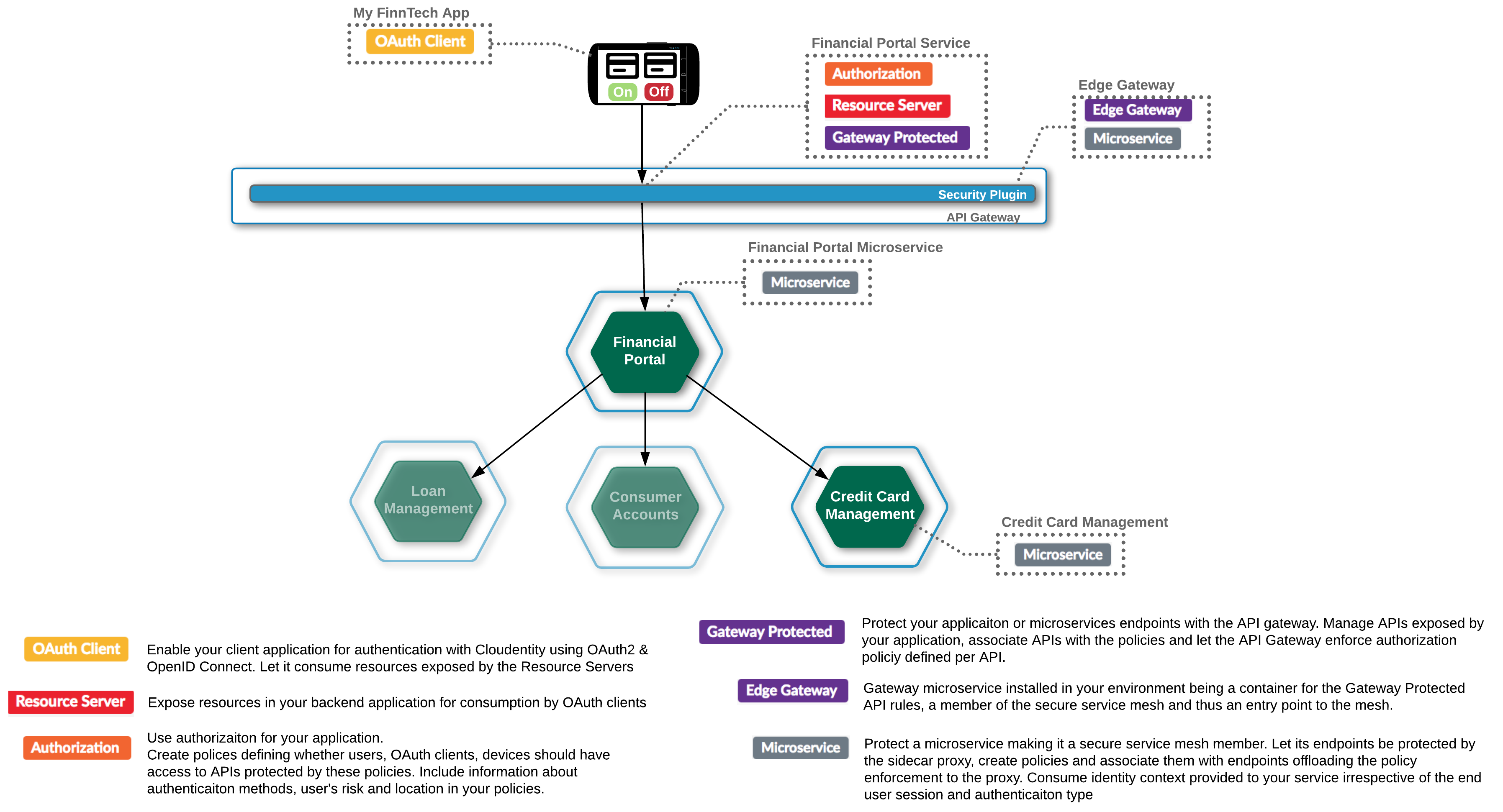
Application is a multi-tenant first class citizen in Cloudentity stack. Each application can have multiple capabilities assigned depending on its purpose (see diagram below).
Configuration
The input configuration to Application Service is meta-config.json file that defines configuration sources (e.g. file, Consul, etc.).
{
"scanPeriod": 5000,
"stores": [
{
"type": "file",
"format": "json",
"config": {
"path": "src/main/resources/config.json"
}
}
]
}Application configuration has following structure:
{
"apiServer": {
"http": {
"port": 7070
},
"routes": [
{
"id": "alive-route",
"method": "GET",
"urlPath": "/alive",
"skipBodyHandler": false
},
...
]
},
"registry:routes": {
"alive-route": { "main": "com.cloudentity.services.mesh.routes.AliveRoute" },
...
},
"registry:components": {
"example-service": { "main": "io.orchis.tools.vertx.jwt.impl.ExampleVerticle" },
...
},
"example-service": {
},
...
}Custom settings
Http Server port configuration:
{
"apiServer": {
"http": {
"port": 7070
}
}
}Default oauth client settings:
{
"register-oauth-client-capability": {
"defaults": {
"grantTypes": [ "refresh_token", "authorization_code" ],
"scope": ["address", "phone", "openid", "email", "profile" ],
"accessTokenValiditySeconds": 3600,
"allowIntrospection": false,
"defaultMaxAge": 60000,
"deviceCodeValiditySeconds": 1800,
"idTokenValiditySeconds": 3600,
"requireAuthTime": true,
"subjectType": "PUBLIC"
},
"appGrantTypes": {
"native": ["authorization_code"],
"web": ["authorization_code", "refresh_token"],
"spa": ["implicit"],
"cli": ["client_credentials"]
}
}
}Default resource server settings:
{
"register-resource-server-capability": {
"defaults": {
"grantTypes": [ "client_credentials" ],
"scope": ["address", "phone", "openid", "email", "profile" ],
"accessTokenValiditySeconds": 3600,
"allowIntrospection": true,
"idTokenValiditySeconds": 0
}
}
}External Dependencies
Application Service requires some external services to be deployed. Below is the list with configuration.
-
Cassandra
{
"cassandra-client": {
"properties": {
"keyspace": "application_service",
"session.contactPoints": ["127.0.0.1"],
"session.withPort": "9042",
"session.queryOptions.consistencyLevel": "LOCAL_QUORUM"
}
}-
LLA Service
{
"lla-client": {
"defaultPort": 8080,
"defaultHost": "localhost",
"basePath": ""
}
}-
Authz Service
{
"authz-client": {
"defaultPort": 9050,
"defaultHost": "localhost",
"basePath": ""
}
}-
Consul
{
"consul": {
"host": "localhost",
"port": 8500
}
}API Access
API Access depends on authz policies enforced by Api Gateway, but default configuration is described below.
Organization admin (user with entitlement ADMIN_MANAGE_APPLICATIONS) can manage applications developed within organization.
To manage user permissions user must have following entitlements: ADMIN_MANAGE_PERMISSIONS, ADMIN_LIST_USER_PERMISSIONS, ADMIN_MODIFY_USER_PERMISSIONS.
If user want to become a developer, admin needs to grant him SELF_ACCESS_APPLICATIONS entitlement.
User after accepting terms of conditions is granted SELF_MANAGE_APPLICATIONS entitlement and can manage only his applications.