Downloading SAML IDP metadata
This article explains how to download SAML IDP metadata from Cloud Identity Plane using either the administrator UI or an API call.
Download CIP SAML metadata
CIP SAML metadata information has to be provided to the SAML-enabled identity providers in order to register CIP as a service provider.
CIP metadata can be downloaded from the CIP system via:
-
Administrator UI
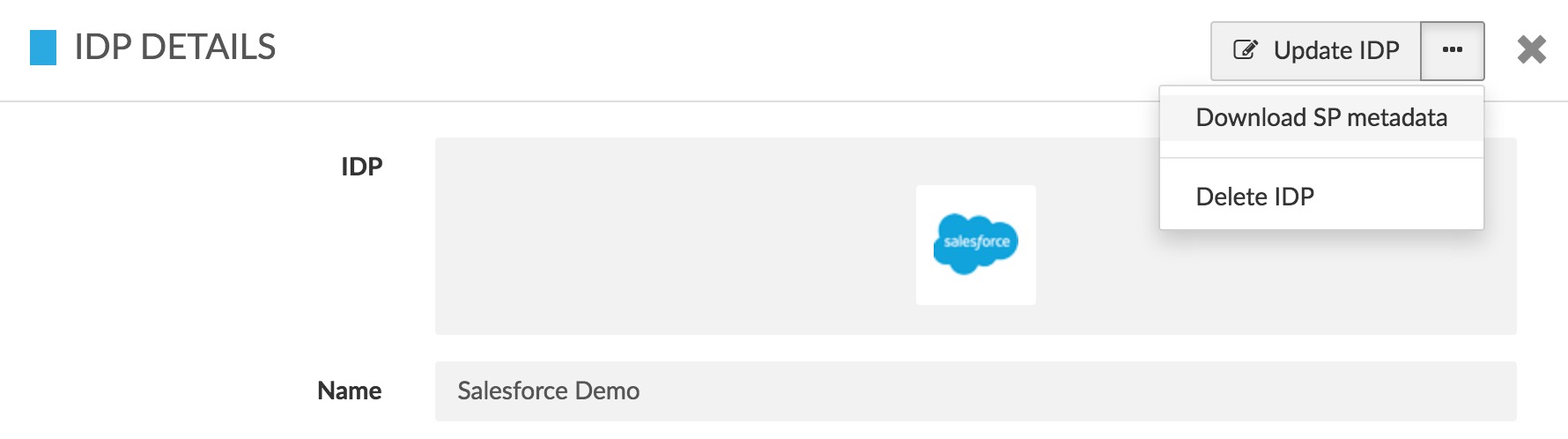
-
API call
Get the metadata
GET https://<cloudentity-saml-idp-host>/saml/metadataGet the certificate
GET https://<cloudentity-saml-idp-host>/saml/certificate
Note
The CIP service provider metadata is available for download only after you have completed the external identity provider registration process within CIP.
Sample metadata
Below you can find a sample of how a SAML metadata file can look like.
<?xml version="1.0" encoding="UTF-8"?>
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:mdui="urn:oasis:names:tc:SAML:metadata:ui" xmlns:shibmd="urn:mace:shibboleth:metadata:1.0" entityID="https://ecs.acme.cloudentity.com/saml">
<IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol urn:oasis:names:tc:SAML:1.1:protocol urn:mace:shibboleth:1.0">
<Extensions>
<shibmd:Scope regexp="false">ecs.acme.cloudentity.com</shibmd:Scope>
</Extensions>
<KeyDescriptor>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>REPLACE_WITH_CLOUDENTITY_IDP_X509_CERTIFICATE</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes128-gcm" />
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes192-gcm" />
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes256-gcm" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc" />
<EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#rsa-oaep" />
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p" />
</KeyDescriptor>
<ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:1.0:bindings:SOAP-binding" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML1/SOAP/ArtifactResolution" index="1" />
<ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/SOAP/ArtifactResolution" index="2" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/Redirect/SLO" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/POST/SLO" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/POST-SimpleSign/SLO" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/SOAP/SLO" />
<NameIDFormat>urn:mace:shibboleth:1.0:nameIdentifier</NameIDFormat>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>
<SingleSignOnService Binding="urn:mace:shibboleth:1.0:profiles:AuthnRequest" Location="https://ecs.acme.cloudentity.com/saml/profile/Shibboleth/SSO" />
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/POST/SSO" />
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/POST-SimpleSign/SSO" />
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/Redirect/SSO" />
</IDPSSODescriptor>
<AttributeAuthorityDescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:1.1:protocol">
<Extensions>
<shibmd:Scope regexp="false">ecs.acme.cloudentity.com</shibmd:Scope>
</Extensions>
<AttributeService Binding="urn:oasis:names:tc:SAML:1.0:bindings:SOAP-binding" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML1/SOAP/AttributeQuery" />
<!-- <AttributeService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/SOAP/AttributeQuery"/> -->
<!-- If you uncomment the above you should add urn:oasis:names:tc:SAML:2.0:protocol to the protocolSupportEnumeration above -->
</AttributeAuthorityDescriptor>
</EntityDescriptor>
SAML metadata terms
| Name | Description | Sample value |
|---|---|---|
| EntityID | Unique name representing the federation agreement | entityID="urn:mace:saml:3b4ts14l0jveaad65c5a" |
| NameIDFormat | Format of the attribute for NameID in SAML response assertion | urn:oasis:names:tc:SAML:2.0:nameid-format:transient |
| SingleSignOnService URL | SAML assertion producer endpoint after login. This value can be found within the Location block of SingleSignOnService. |
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ecs.acme.cloudentity.com/saml/profile/SAML2/POST/SSO"/> |